Unknown Keylogger Embedded in Microsoft Exchange Server Detected by Positive Technologies
While investigating a security incident for one of its clients, researchers at Positive Technologies discovered a previously unknown keylogger embedded in the main page of Microsoft Exchange Server. This malicious software collected account login data and stored it in a file accessible via a special path from the internet.
Scope of the Attack and Victims
Further analysis revealed more than 30 victims across different countries, most of which were government organizations. The earliest compromise dates back to 2021. Due to a lack of additional data, the attacks could not be linked to specific hackers. However, it was noted that most victims were located in African and Middle Eastern regions.
Attack Methodology
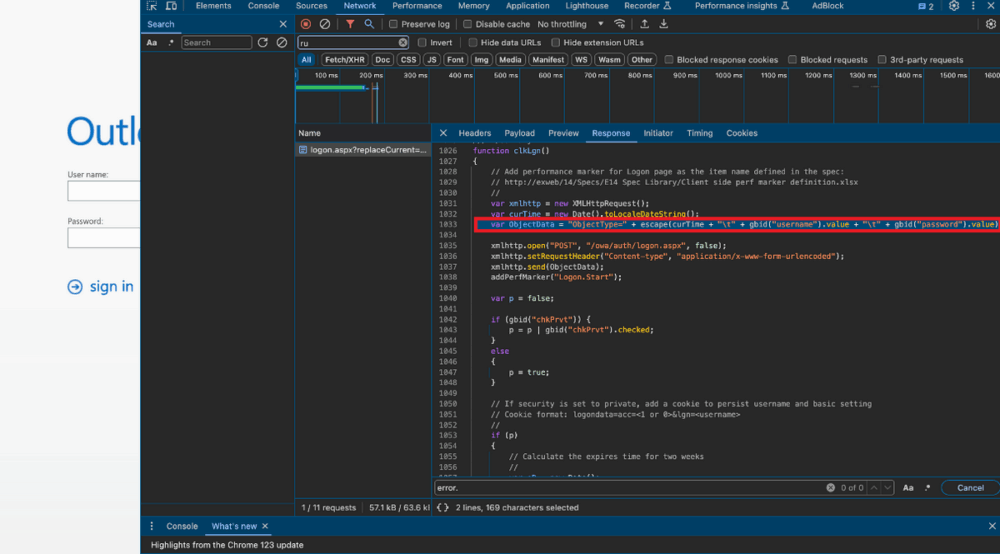
To implant their stealer, the hackers exploited known vulnerabilities in Exchange servers—specifically, the ProxyShell vulnerabilities. They then added the keylogger to the main page, within the clkLgn() function.
Additionally, the attackers modified the logon.aspx file by inserting code that processed the stealer’s results and redirected all entered account credentials to a special file accessible from outside the network.
Consequences and Affected Sectors
This allowed the attackers to access all user-entered account credentials. In total, more than 30 victims were identified. In addition to government agencies, affected organizations included banks, IT companies, and educational institutions. The targeted countries included Russia, the UAE, Kuwait, Oman, Niger, Nigeria, Ethiopia, Mauritius, Jordan, Lebanon, and others. All affected parties have already been notified of the compromise.