0-Day Vulnerability Patched in Telegram for Windows
The desktop version of Telegram for Windows has patched a zero-day vulnerability that could have been used to bypass security warnings and automatically launch Python scripts. According to Bleeping Computer, rumors about a vulnerability in Telegram that allowed arbitrary code execution on a victim’s machine surfaced last week on social media and hacker forums.
While some claimed the vulnerability required no user interaction, demonstration videos showed someone clicking a received file in Telegram to launch the Windows calculator. At that time, Telegram representatives quickly denied the existence of such a vulnerability, stating they “could not confirm the existence of this issue,” and suggested the videos were likely fake.
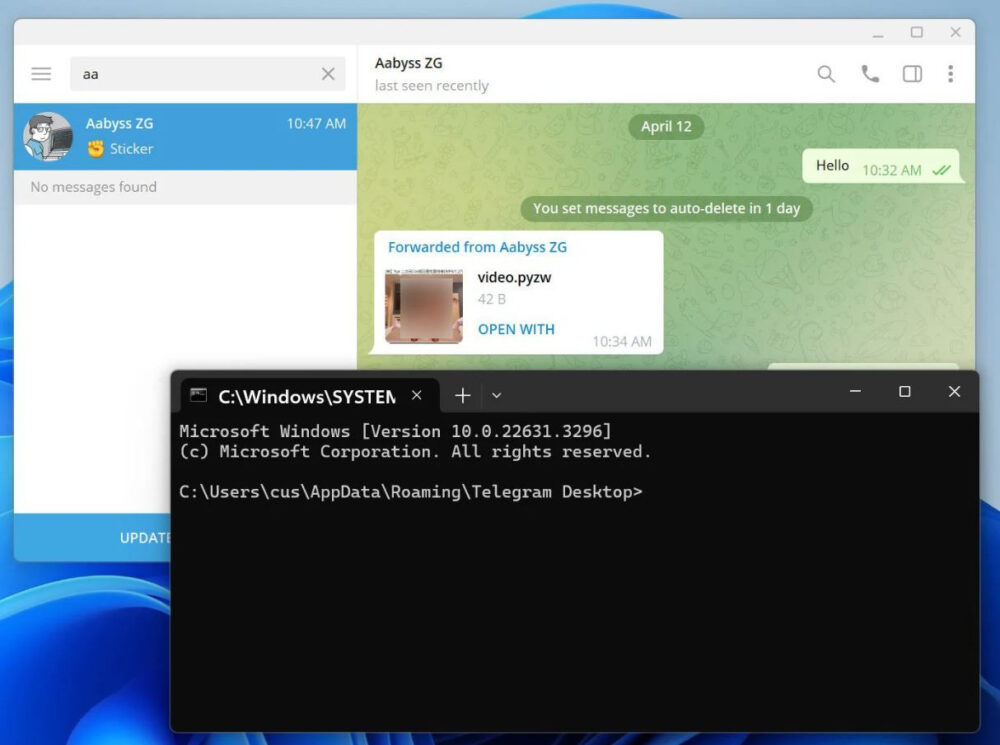
Soon after, however, a proof-of-concept exploit was posted on the XSS hacker forum. It explained that due to a typo in the Telegram for Windows source code, users could send Python .pyzw files that, when clicked, would bypass security warnings. As a result, the .pyzw file would execute automatically, and Telegram would not display any warning, unlike with other executable files where a warning is expected. Normally, when launching a file with a potentially dangerous extension (a list of which can be found here), the messenger displays a warning that the file may harm the user’s computer.
How the Exploit Worked
Files of unknown types shared via Telegram can be automatically launched in Windows, allowing the OS to decide which program to use. Worse, the exploit posted on XSS disguised the Python file as a video with a preview, making it easier to trick users into clicking the fake file.
In a conversation with Bleeping Computer, Telegram developers said they have already fixed the issue, and now automatic execution of Python scripts when clicking the file no longer works. The company also emphasized that this was not a zero-click vulnerability; user interaction was still required.
“Rumors about a zero-click vulnerability in Telegram Desktop are not true. Some ‘experts’ recommended disabling automatic downloads in Telegram, but there were no issues that automatic downloads could have triggered.
However, a problem was found in Telegram Desktop that required the user to click a malicious file, provided Python was installed on the computer. Contrary to previous reports, this was not a zero-click vulnerability and could only affect a small portion of our user base: less than 0.01% of our users have Python installed and use the relevant version of Telegram Desktop.
We have implemented a server-side fix to ensure that even this issue is no longer reproducible, so all versions of Telegram Desktop (including older ones) are now safe from this vulnerability,” the company stated.
Root Cause: A Simple Typo
As Bleeping Computer explains, developers were aware that .pyzw files, intended for Python zipapps, could pose a threat. However, the extension .pywz (not .pyzw) was included in the list of dangerous extensions due to a simple typo.
Journalists note that developers were notified of the bug on April 10 and fixed it by correcting the typo in the data_document_resolver.cpp file. However, this fix is not yet active, and clicking the file still does not show a warning. Instead, Telegram has temporarily solved the problem server-side by adding the .untrusted extension to all .pyzw files. This means that when users click these files, Windows will ask which program to use and will not automatically launch them with Python.
In future versions of the Telegram desktop app, standard warnings about potentially dangerous files are expected to work as intended, and the need for the .untrusted extension will be eliminated.