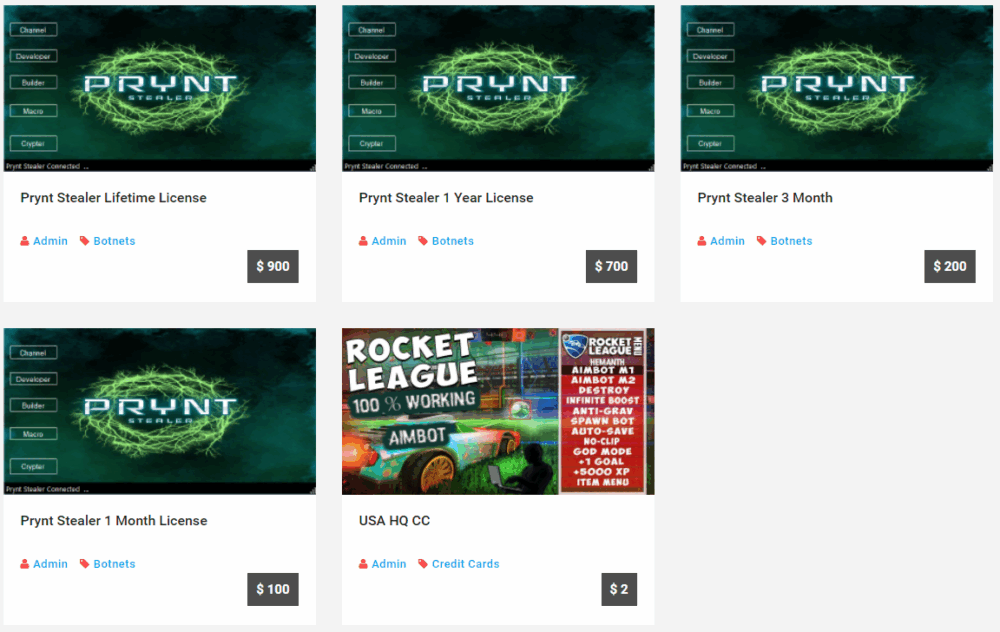
Prynt Stealer Malware Sold on the Dark Web for Just $100 a Month
Cybersecurity experts from Cyble have discovered a new information-stealing malware called Prynt Stealer. This malware offers extensive capabilities and comes with additional keylogger and clipper modules. Prynt Stealer is marketed as a solution for compromising a wide range of browsers, messengers, and gaming applications, and it is also capable of carrying out direct financial attacks.
Prynt Stealer is distributed via a subscription model, with its creators charging $100 per month, $200 per quarter, or $700 per year. A lifetime license is also available for $900. Additionally, buyers can use a builder tool to create their own compact and hard-to-detect version of the malware, which can be used in targeted attacks.
Stealth Features and Technical Details
According to Cyble analysts, Prynt Stealer was designed with stealth in mind. It uses binary obfuscation and string encryption with Rijndael. All communications with command-and-control servers are encrypted using AES256, and the AppData folder (and its subfolders), which is used for temporarily storing stolen data, is hidden.
Once it infects a victim’s machine, Prynt Stealer scans all disks on the host and steals documents, database files, source code, and image files smaller than 5,120 bytes (5 KB). The malware then targets Chrome-based browsers, Firefox, and MS Edge, stealing autofill data, credentials, banking card information, browsing history, and cookies. At this stage, the malware uses the ScanData() function to search browser data for keywords related to banks, cryptocurrencies, and adult sites, stealing any relevant information it finds.
Targeting Messengers and Gaming Platforms
Next, Prynt Stealer attacks messengers, including Discord, Pidgin, and Telegram, stealing Discord tokens if they are present on the system. It also steals authentication files for gaming applications, game save files, and other valuable data from Ubisoft Uplay, Steam, and Minecraft.
Finally, the malware queries the registry to find data from cryptocurrency wallets such as Zcash, Armory, Bytecoin, Jaxx, Ethereum, AtomicWallet, Guarda, and Coinomi. It also steals information from FileZilla, OpenVPN, NordVPN, and ProtonVPN, copying the relevant credentials into the aforementioned hidden AppData subfolder.
System Profiling and Data Exfiltration
Before stealing data, Prynt Stealer performs general system profiling, including creating a list of running processes, taking a screenshot, and linking the collected information to network credentials and the Windows key used on the victim’s machine. Data exfiltration is carried out via a Telegram bot, which uses an encrypted network connection to upload the dump to a remote server.
As mentioned above, in addition to these features, the malware includes keylogger (to capture keystrokes) and clipper (to monitor and replace cryptocurrency addresses in the clipboard) modules.
Conclusion
Experts conclude that the new Prynt Stealer is a highly dangerous piece of malware that can steal confidential user data, lead to significant financial losses, compromise accounts, and cause data leaks.