Phoenix Keylogger Can Disable Over 80 Security Products
Researchers at Cybereason have analyzed the Phoenix malware, which appeared in the summer of this year and is a hybrid of a keylogger and an infostealer. The malware is distributed via the MaaS (malware-as-a-service) model and is already responsible for 10,000 infections.
Phoenix is sold as a subscription-based product, with prices ranging from $14.99 per month to $78.99 for a lifetime subscription.
Phoenix Control Panel
According to Cybereason analysts, Phoenix is the work of an experienced malware developer. It appears that the original creator was also behind Alpha Keylogger, who passed away earlier this year.
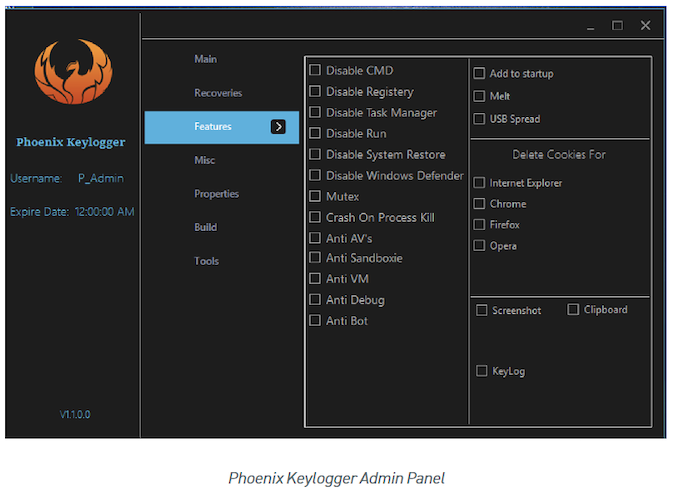
Over the past few months, Phoenix has evolved from a simple keylogger into a multifunctional trojan designed for information theft (infostealer). While early versions only intercepted keystrokes, newer versions can steal passwords from nearly twenty different browsers, four email clients, FTP clients, and messengers. The malware can also steal clipboard data, take screenshots, and download additional malicious programs.
Stolen information is sent to the malware operators via SMTP, FTP, or Telegram.
Anti-Antivirus and Anti-VM Capabilities
Phoenix has also acquired aggressive modules targeting antivirus software and virtual machines, aiming to prevent detection and analysis. Both modules work similarly: they attempt to terminate a range of processes before the malware continues its operation, using a predefined list of process names. This list includes the names of over 80 well-known security products and virtual machines commonly used for reverse engineering and malware analysis.
Short-Term Use and Data Theft
Analysts note that Phoenix could use its capabilities to achieve persistent presence on a system, but its operators are not interested in this. According to researchers, the malware is most often used as a one-time solution for data theft and is not employed for long-term surveillance of victims. Within seconds of infection, Phoenix steals all the necessary confidential data, and its job is done. The stolen information is most often sold on the dark web.