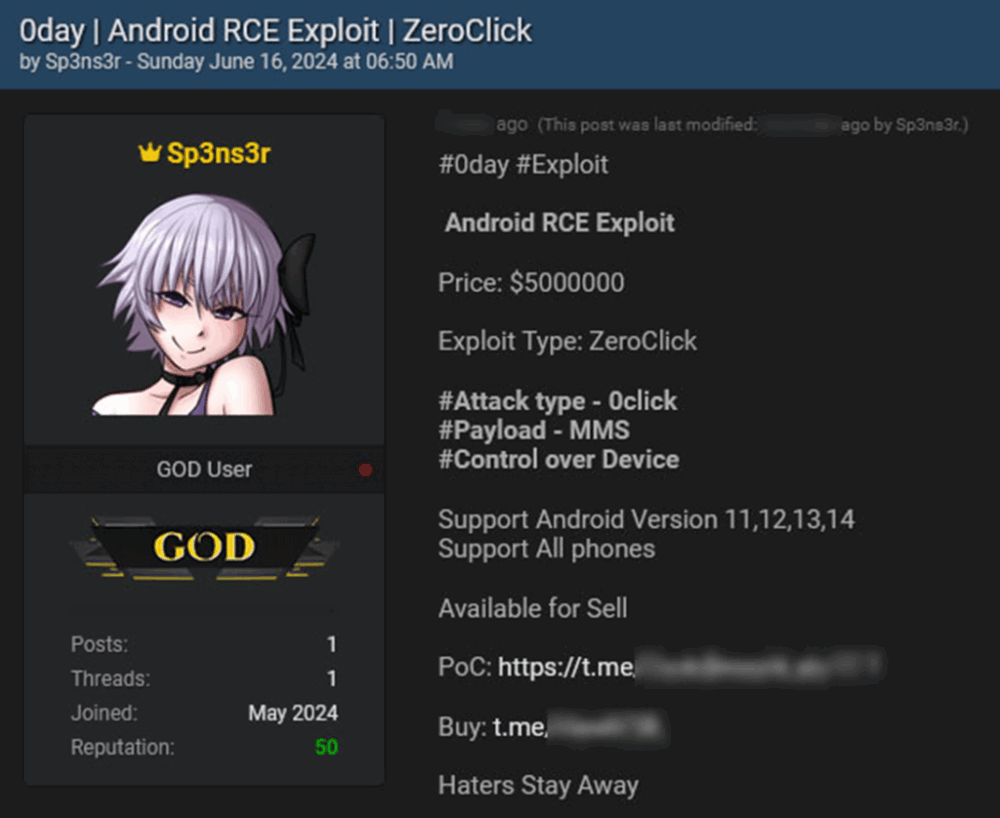
New Zero-Click RCE Exploit for Android Listed for $5 Million
On June 16, 2024, a cybercriminal using the alias “Sp3ns3r” announced the sale of a high-level zero-day remote code execution (RCE) exploit on the cybercrime marketplace BreachForums. The seller emphasized the simplicity of the attack, highlighting its zero-click nature—meaning the exploit requires no user interaction to execute code on the target device.
Exploit Details
According to the hacker, the exploit supports Android operating systems versions 11, 12, 13, and 14, demonstrating effectiveness across all Android devices. The potential scale of the threat is extremely high.
The main method of distribution is through MMS (Multimedia Messaging Service) messages. Simply receiving such a message is enough to infect your device. Because this is an RCE exploit, a remote attacker can execute any commands on the compromised device after infection.
The exploit is being offered for a record-breaking $5 million. Additionally, the hacker is providing a proof of concept (PoC) upon request to demonstrate the exploit’s capabilities.
Previous Records and Context
The previous record for the most expensive exploit listed for sale was an RCE vulnerability in Microsoft Outlook, which was offered on the same BreachForums for $1.7 million. This new Android exploit has now officially surpassed that record.
How to Protect Your Android Device
To protect your Android device from this new zero-click attack, you can disable automatic MMS downloads in your messaging settings. In Google Messages, follow these steps:
- Tap your avatar.
- Go to “Messages” app settings.
- Select your SIM card.
- Find “Auto-download MMS” and switch the toggle to “Off.”
Staying Safe Against Zero-Click Exploits
The emergence of this advanced zero-click exploit for Android shows that cybercriminals are constantly seeking new ways to attack and monetize vulnerabilities. Users should remain vigilant, keep their software up to date, and follow cybersecurity best practices to protect their devices and data.