Mars Infostealer Spreads Through OpenOffice Ads on Google
The recently emerged Mars infostealer is just starting to gain popularity in hacker circles, but analysts are already noting the first large-scale campaigns using it. Mars is a reworked version of the Oski malware, whose development was discontinued in 2020. This malicious software has extensive capabilities for stealing information and targets a wide range of applications, including popular browsers, two-factor authentication plugins, as well as numerous extensions and wallets for working with cryptocurrencies.
What Data Does Mars Steal?
Mars also collects and sends the following information about the victim’s system to its operators:
- IP address and country
- Path to the EXE file
- Local time and time zone
- System language
- Keyboard layout
- Laptop or desktop
- Processor model
- Computer name
- User name
- Domain computer name
- Machine identifier
- GUID
- Installed programs and their versions
Mars Admin Panel and Growing Popularity
Until recently, Mars was advertised on many hacker forums for $140 to $160 for a lifetime license and was growing rather slowly. However, the recent shutdown of Raccoon Stealer seems to have forced hackers to look for alternatives and turn their attention to Mars. The malware’s authors even stated that they were barely able to keep up with the influx of new customers.
Distribution Methods
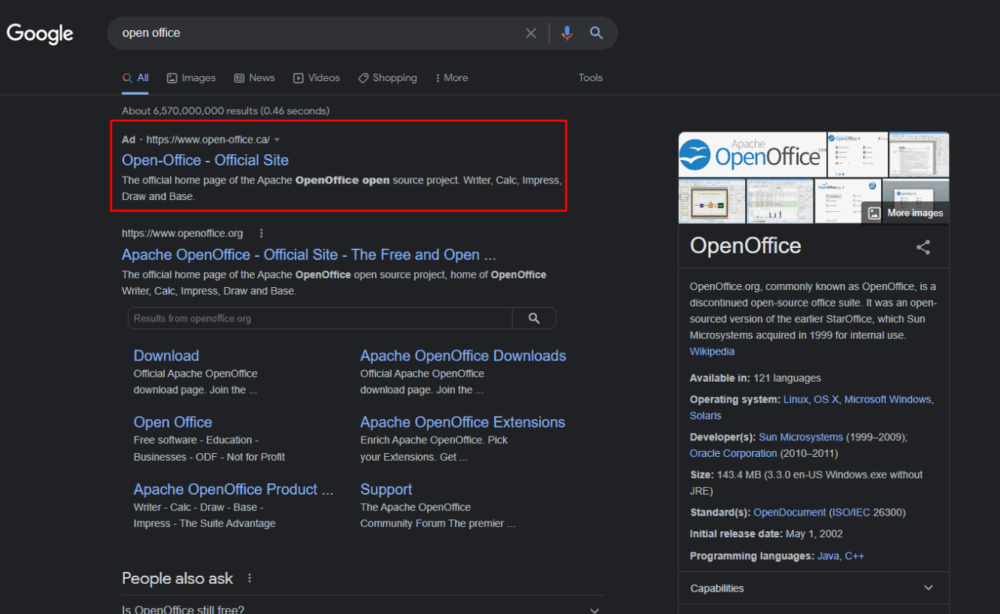
Most often, this malware is distributed through spam emails containing an executable file in an archive, a download link, or a malicious document. However, Mars is sometimes spread through fraudulent websites. One such campaign, which has become more common with the increase in customers, was discovered by experts at Morphisec. According to their data, the malware uses Google Ads to push clone sites of the open-source OpenOffice project to the top of search results in Canada. The OpenOffice installer on such a fake site is actually a Mars executable, packed with the Babadeda cryptor or the Autoit loader.
Leaked Version and Operator Mistakes
Interestingly, soon after Mars was released, a cracked version of the malware appeared with instructions that had serious flaws. In particular, the instructions advised setting full access (777) to the entire project, including the directory with victim logs.
The logs are ZIP files containing data stolen by the malware from users and uploaded to the command server. The error in the instructions led to attackers misconfiguring their environment, exposing important information to the public. Researchers found that, in the campaign mentioned above, the stolen information included browser autofill data, browser extension data, banking card information, IP address, country code, and time zone.
Operator Exposes Himself
Because the malware operator followed the instructions and infected himself with Mars (apparently during debugging), his personal data was also exposed. This mistake allowed Morphisec experts to link the attacks to a Russian-speaking user, discovering his GitLab accounts, stolen credentials used to pay for Google Ads, and much more.
Victims and Impact
The Morphisec Labs team reports that they were able to identify more than 50 infected user domains in total, with compromised domain passwords for their companies. The vast majority of victims are students, teachers, and content creators who were searching for legitimate applications but instead received malware. Morphisec also managed to extract credentials that led to the full compromise of an unnamed Canadian infrastructure solutions provider and several well-known Canadian service companies. Experts have already contacted the affected parties and notified authorities about the incidents.