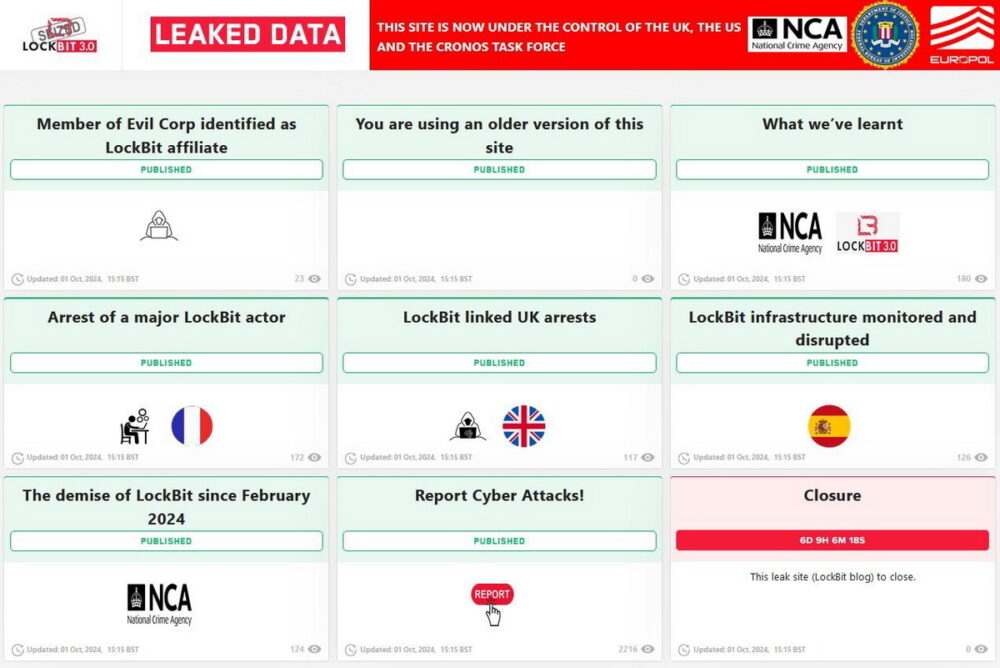
Four Arrested in Connection with LockBit Hacker Group
Law enforcement agencies have announced a new phase of Operation Cronos and the arrest of four suspects allegedly linked to the LockBit hacker group. Among those detained are a developer, the administrator of the group’s “bulletproof” hosting service, and two other suspects.
Back in February 2024, authorities carried out a large-scale Operation Cronos, disabling the infrastructure of the LockBit ransomware group. This included taking down 34 servers that hosted data leak sites, their mirrors, stolen victim files, and cryptocurrency wallets.
Authorities also reported obtaining several thousand decryption keys, after which a free tool was released to help victims restore their files.
In May of this year, after analyzing data seized in February, the FBI, the UK’s National Crime Agency (NCA), and Europol published extensive charges and imposed sanctions against 31-year-old Russian citizen Dmitry Yuryevich Khoroshev. At the time, law enforcement claimed he was the person behind the aliases LockBitSupp and putinkrab, acting as the administrator and developer of the ransomware group.
Authorities stated that LockBit extorted over $1 billion from thousands of companies worldwide, with Khoroshev and his associates receiving more than $500 million in ransom payments from their victims.
This week, websites previously hacked by law enforcement at the start of the year became active again. Europol, the NCA, and the U.S. Department of Justice announced that in August 2024, they managed to arrest an alleged LockBit developer at France’s request while he was on vacation outside Russia. French law prohibits disclosing the identity of the arrested individual, and the country where the suspect was detained has not been revealed.
In the UK, around the same time, two LockBit “partners” were arrested, one of whom was allegedly involved in money laundering. Their identities were established after analyzing a large amount of data obtained in February.
Spanish authorities also arrested the suspected administrator of the group’s “bulletproof” hosting service at Madrid airport, which allowed them to seize nine servers that were part of LockBit’s infrastructure. According to an official Europol statement, this individual “was one of the main people responsible for LockBit’s infrastructure,” and the information obtained from the seized servers will be useful in future efforts to prosecute key members and partners of the hacker group.
Additionally, yesterday authorities in Australia, the UK, and the U.S. announced new sanctions against several individuals believed to be involved in spreading LockBit, as well as those connected to another notorious hacker group, Evil Corp.
- The UK imposed sanctions on 16 Russian citizens.
- The U.S. imposed sanctions on six more individuals.
- In Australia, sanctions affected two people.