800,000 Russians Victimized by Geost Android Banking Botnet
Researchers from the Czech Technical University, UNCUYO University, and Avast have investigated the Geost Android botnet and the history of its creators, presenting their findings at the Virus Bulletin 2019 conference.
The exposure of this banking botnet, which targeted Russian residents, was made possible by a series of mistakes made by the criminals. According to the researchers, the Geost botnet has been active since 2016, has already infected over 800,000 Android devices, and may have controlled several billion rubles.
How the Botnet Was Discovered
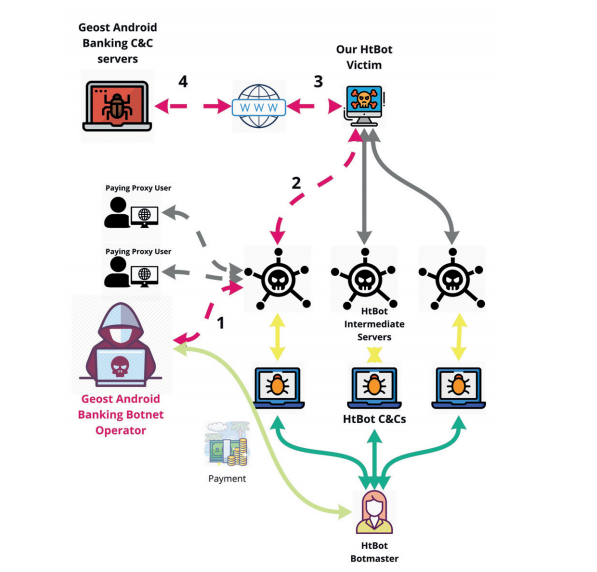
The discovery came after hackers decided to use a malicious proxy network created with the HtBot malware. This proxy service can be rented to allow users to communicate pseudo-anonymously online. Analysis of HtBot’s network traffic led to the uncovering of a large-scale malicious campaign that affected more than 800,000 Android devices.
The attackers made poor choices in anonymization platforms to cover their tracks. They failed to encrypt their messages, which allowed researchers to learn details about their internal operations. The uncovered chats revealed how hackers accessed servers, added new devices to the botnet, and evaded antivirus software. Most notably, researchers were even able to access the criminals’ personal conversations.
In one Skype chat, a group member said he wanted to leave, but the team leader persuaded him to stay: “Alexander, if we started together, we need to finish the job together. It’s working now, and we can make money. We don’t get 100,000 for promotion every day.”
Researchers were not entirely sure what was meant by “promotion,” as the conversation also mentioned money laundering and payments using systems popular among Russian-speaking cybercriminals. Further analysis showed how hackers added devices to the botnet and delivered the banking trojan to victims’ bank accounts.
“We gained truly unprecedented insight into how such groups operate,” said Anna Shirokova, an Avast researcher. “Because this group failed to hide their actions, we were able to see not only malware samples but also understand how hackers work with lower-level spyware that connects devices to the botnet. In total, there have already been more than 800,000 victims. Preliminary data suggests the group may have controlled millions in currency.”
The Geost Botnet and Banking Trojan
The botnet, named Geost by researchers, is a complex infrastructure of infected Android devices. The attackers used legitimate apps from the Google Play Store as a base, edited the code to add malicious features to the real app functionality, and then uploaded these apps to third-party Android stores. These fake apps often imitated games, banking apps, and social networking apps.
Once this malware is installed on a phone, it becomes part of the botnet and can be controlled remotely. Typically, attackers can access SMS messages, send texts, communicate with banks, and redirect the phone’s traffic to various websites. Hackers also gain access to a large amount of personal user information. Sometimes, the malware operators also displayed fake pop-up windows asking for login credentials.
After infection, the command server saves a complete list of the victim’s SMS messages from the moment the device is compromised. These SMS messages are then processed offline on the command server to automatically calculate each victim’s account balance. After processing, the malware operators can identify which victims have the largest account balances.
The botnet has a complex infrastructure, including at least 13 IP addresses, over 140 domains, and more than 150 APK files. The main targets of the banking trojan were five banks, mostly located in Russia. Two of these banks operate in Western and Eastern Europe, and one is part of a holding company with branches in 15 countries.
Since Geost is still active, researchers plan to continue using their knowledge of the group to monitor its activities. Despite the attackers’ poor operational security, they still have access to a vast network of infected devices.