Tesla NFC Key Vulnerability Lets Thieves Add New Keys in 130 Seconds
On June 12, 2022, Austrian researcher Martin Herfurt demonstrated a new method for stealing Tesla vehicles. He discovered that it’s possible to exploit the process of adding a new NFC key card, doing so without the car owner’s knowledge in just 130 seconds.
How the Vulnerability Works
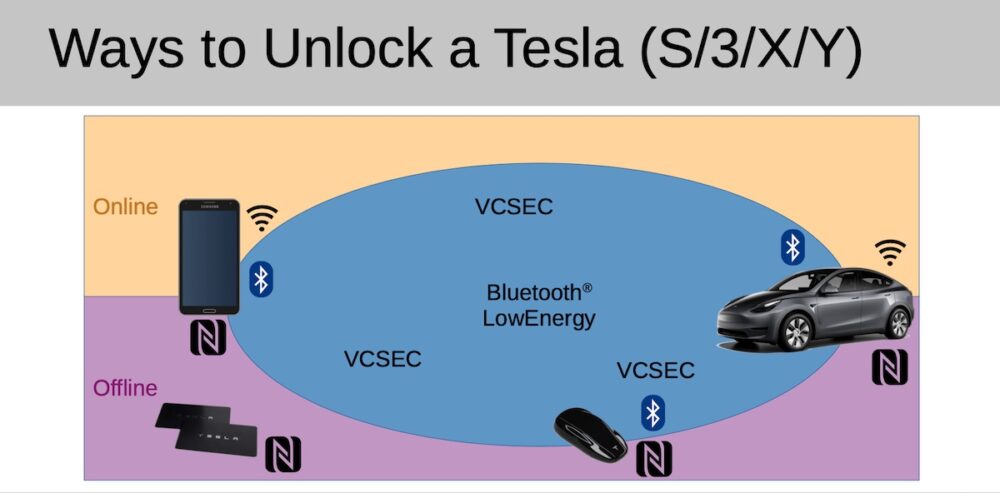
The root of the problem lies in a Tesla update released last year, which made it easier to start cars after unlocking them with NFC key cards. Previously, drivers using a key card had to place it on the center console to start driving. However, after an update in August, Tesla owners could drive immediately after unlocking with the key card—one of three ways to unlock a Tesla (the other two are a key fob and the mobile app).
Herfurt found that this new feature has a strange side effect: not only does it allow the car to start automatically within 130 seconds of unlocking, but it also puts the car into a state where it will accept entirely new keys—without any authentication and without any indication on the car’s display.
“Tesla introduced this timer to make using NFC cards more convenient, so the car could start and drive without the user having to use the key card again. But there’s a problem: during the 130-second window, not only is driving allowed, but also the registration of a new key,” the expert explains.
How Attackers Can Exploit the Bug
The official Tesla app does not allow new keys to be registered unless it’s connected to the owner’s account. However, Herfurt discovered that the car will communicate with any nearby Bluetooth Low Energy (BLE) device. He created his own app, called Teslakee, which uses the same VCSec protocol as the official Tesla app.
Teslakee demonstrates how easily thieves can add their own key to a Tesla. They simply need to be near the car during the 130-second window after it’s unlocked with an NFC key card. After that, the thief can use their key to unlock, start, and stop the car at any time. No messages or warnings appear on the car’s display or in the official Tesla app.
If the owner usually unlocks the car with the app (the most common method), an attacker can force the victim to use the key card by jamming the BLE frequency needed for the app to work. This can be done with a simple signal jammer.
Herfurt successfully tested his attack on Tesla Model 3 and Model Y. He did not test it on the newer Model S and X, but suspects they are also vulnerable since they use the same technology. A demonstration of the attack is available in the video below.
Research Background and Tesla’s Response
Herfurt developed Teslakee and conducted his research as part of Project Tempa, which “provides tools and information about the VCSEC protocol used by Tesla accessories and apps to control vehicles via Bluetooth LE.” He is also a member of the Trifinite Group, a research and hacker collective focused on BLE security.
The researcher made the vulnerability public because, according to him, Tesla is unlikely to fix it. Herfurt says he never received any response from the company regarding vulnerabilities he reported in 2019 and 2021, and doubts anything will change now. “I got the impression they already knew about everything and didn’t want to change anything,” Herfurt says. “This time, Tesla also can’t be unaware of this poor implementation. So I just don’t see the point in contacting Tesla in advance.”
What Tesla Owners Can Do
Since Tesla has not commented on Herfurt’s findings, there’s unfortunately not much owners can do to protect themselves. One possible defense is enabling Pin2Drive, which prevents the car from being started without a PIN, though this won’t stop a thief from entering the vehicle. Owners should also regularly check the list of keys authorized to unlock and start their car.