SilkSpecter Steals Credit Card Data via Fake Online Stores
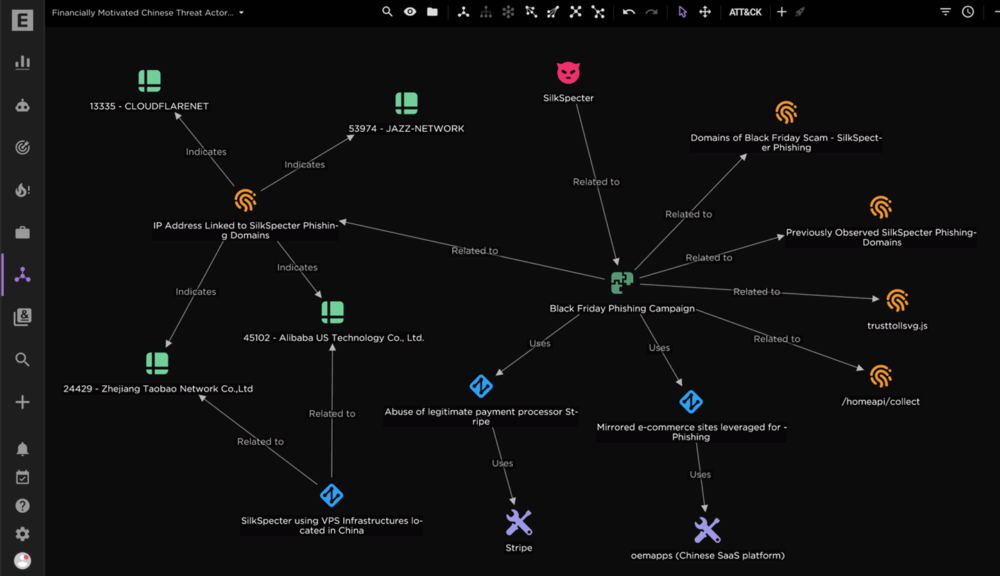
Researchers at EclecticIQ have discovered that the Chinese hacker group SilkSpecter has created over 4,000 fake online stores aimed at stealing credit card data from users in the United States and Europe. This campaign, which involves a total of 4,695 domains, began in October 2024. The fake stores offered large discounts ahead of Black Friday, a period known for increased shopping activity.
The malicious websites impersonate well-known brands, including The North Face, Lidl, Bath & Body Works, L.L. Bean, Wayfair, Makita, IKEA, and Gardena. In many cases, the domain names include the phrase “Black Friday,” clearly targeting shoppers looking for deals.
How the Scam Works
According to researchers, SilkSpecter’s sites are well-designed and appear legitimate at first glance. However, they use top-level domains such as .shop, .store, .vip, and .top, which are not typically associated with major brands or trusted retailers. Depending on the victim’s location, the sites use Google Translate for automatic translation.
Additionally, the phishing stores integrate a real Stripe payment system, which adds to their apparent legitimacy but does not prevent the attackers from stealing credit card information.
Tracking and Data Collection
Experts report that SilkSpecter uses tracking tools like OpenReplay, TikTok Pixel, and Meta Pixel on their sites. These tools help monitor visitor behavior, allowing hackers to adjust their tactics for greater effectiveness.
When a user attempts to make a purchase, they are redirected to a payment page where they are asked to enter their credit card number, expiration date, and CVV code. At the final stage of the “checkout” process, the site also requests a phone number.
Researchers believe that the hackers collect phone numbers for use in future phishing attacks, which may help them bypass two-factor authentication when using stolen cards.
Consequences and Attribution
In summary, SilkSpecter not only steals the victim’s money by abusing Stripe but also captures the entered credit card details, which are then sent to a server controlled by the attackers.
Experts link SilkSpecter to China based on the use of Chinese IP addresses and ASNs, Chinese domain registrars, linguistic markers in the code, and the group’s previous use of the Chinese SaaS platform oemapps.