Malicious Tor Browser Version Steals Cryptocurrency from Darknet Market Users
A malicious version of the Tor browser is stealing cryptocurrency from users of darknet markets and tracking the websites they visit. According to ESET experts, cybercriminals registered three cryptocurrency wallets back in 2017, which have since received $40,000 in Bitcoin.
The attackers promote their malicious Tor variant on Pastebin, advertising it as a “Russian-language version” of the browser. Their promotional posts are optimized to appear at the top of search results for queries like drugs, cryptocurrency, bypassing blocks, and Russian politicians. Potential victims are enticed by claims that this version of the browser can allegedly bypass CAPTCHA challenges.
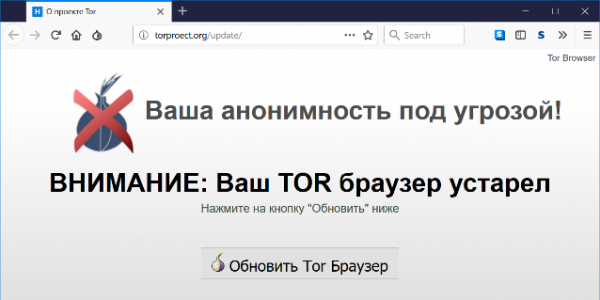
Another method of spreading the malware is through spam emails. Disguised as the “official Russian version,” the malicious browser is downloaded from domains such as tor-browser[.]org and torproect[.]org, which were registered in 2014. The design of these sites is copied from the legitimate Tor ProjectThe Tor Project is a nonprofit organization dedicated to protecting online privacy and ensuring uncensored access to the internet. Emerging from U.S. Naval Research Lab experiments with onion routing in the 1990s, Tor evolved into a decentralized, volunteer-powered network that hides user identities by routing traffic through multiple encrypted relays. Since the launch of the Tor Browser in 2008, it has become a crucial tool for activists, journalists, and everyday users worldwide—supporting free expression during events like the Arab Spring and proving resilient in the face of mass surveillance disclosures. Today, Tor is sustained by a global community committed to human rights, transparency, and digital freedom. More website. When users visit these sites, regardless of the Tor version they are using, they see a notification claiming their browser is outdated and needs to be updated.
If the user chooses to “update” their browser, a script is downloaded to their system that can modify web pages. Specifically, it steals content from forms, hides original content, displays fake messages, and adds other content. This allows the malware to substitute the cryptocurrency wallet address in real time, so any cryptocurrency sent by the user goes to the attackers instead. The script can also steal Qiwi wallet data.
When a victim tries to deposit cryptocurrency, the script replaces their wallet address with one belonging to the attackers. Since cryptocurrency addresses are long strings of random characters, users often do not notice the substitution.