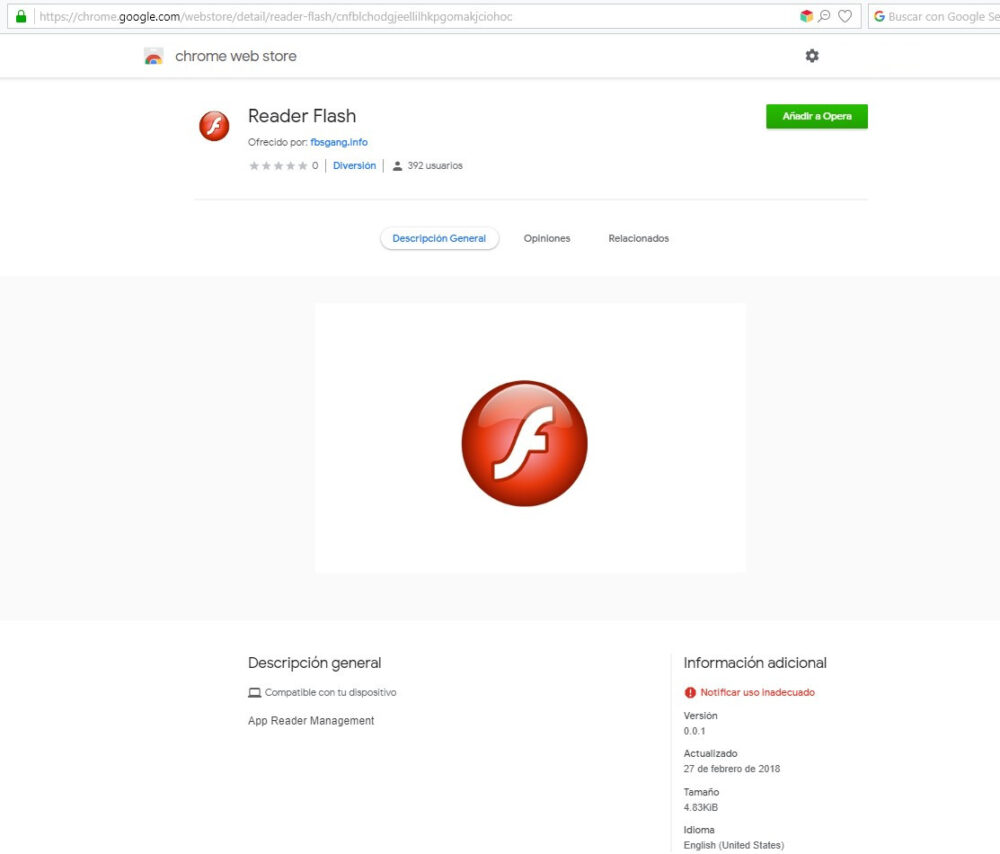
Malicious Chrome Extension Stole Users’ Credit Card Information
Cybersecurity experts from Telefonica’s ElevenPaths division have discovered a malicious extension called Flash Reader (a fake Flash Player) in the official Chrome Web Store. This extension was capable of stealing users’ credit card information. Notably, the malware was uploaded to the store back in February 2018 and was used by around 400 people before being detected.
How the Malicious Extension Spread
According to the experts, the extension was initially distributed through a now-defunct page at http://fbsgang[.]info/flashplayer/. Cybercriminals likely redirected victims to this page using malicious ads or exploit kits. The attackers used a classic trick: displaying a message urging users to urgently install Flash Player to continue working. The provided link led users to the Flash Reader page in the Chrome Web Store.
How the Extension Stole Data
The malicious extension intercepted any content users entered into forms on any website, with a particular focus on Visa, Mastercard, American Express, and Discover card numbers. As soon as the malware detected card information, the collected data was sent to a command-and-control server at http://fbsgang[.]info/cc/gate.php, which is currently offline.
Ongoing Risks and Google’s Response
It’s important to note that as of January 15, 2019, when ElevenPaths published their report, the extension was still available in the official Chrome Web Store. This means that even though the command server was inactive, users were not necessarily safe, and the criminals could have launched a new campaign at any time. Google engineers have since removed Flash Reader from the Chrome Web Store.
Details and Expert Opinions
Researchers noted that the malware only collected card numbers, ignoring cardholder names, CVV codes, and other data. Given that the extension was installed by only about 400 users, experts believe Flash Reader was likely a test tool used by unknown hackers preparing for a larger campaign.