Hackers Can Compromise Accounts Before They’re Even Registered
Microsoft Security Response Center analyst Andrew Paverd and independent cybersecurity expert Avinash Sudhodanan have described an interesting type of attack called pre-hijacking, in which hackers can compromise accounts on services like LinkedIn, Zoom, WordPress, Dropbox, and others even before the legitimate user registers them.
In total, the experts studied 75 popular online services and found that at least 35 of them are vulnerable to pre-hijacking attacks.
“The consequences of pre-hijacking attacks are exactly the same as account takeovers. Depending on the nature of the targeted service, a successful attack can allow an attacker to read or modify confidential information associated with the account (such as messages, payment documents, usage history, etc.), or perform actions using the victim’s identity (for example, sending fake messages, making purchases using saved payment methods, and so on),” the authors explain.
How Pre-Hijacking Attacks Work
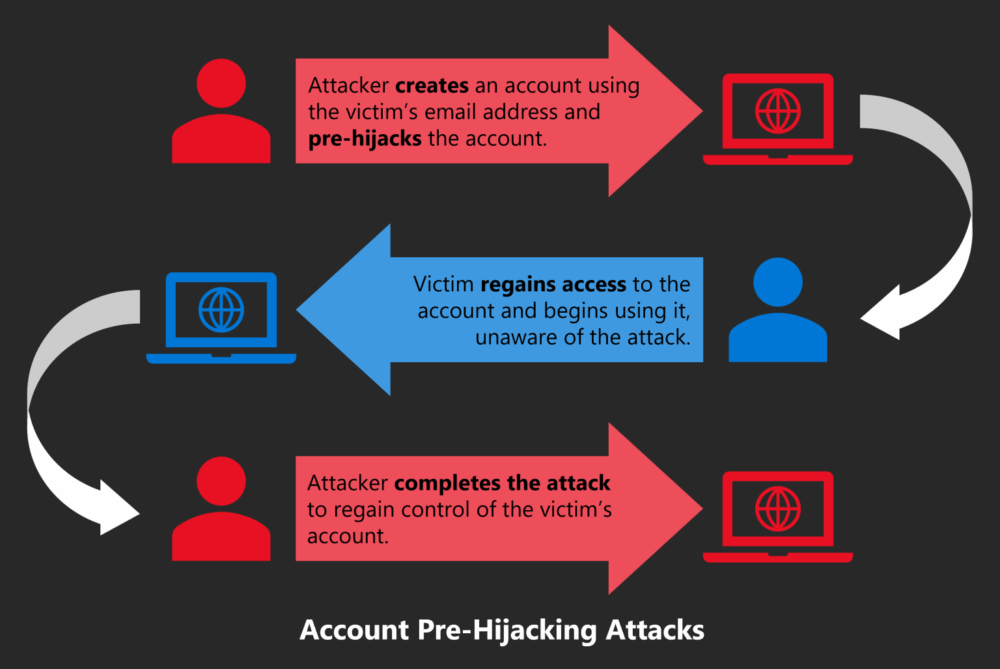
For this attack to work, the hacker needs to know the future victim’s email address, which is often easy to obtain through correspondence or thanks to the many data leaks that occur almost daily. The attacker then creates an account on a vulnerable site using the victim’s email address, hoping the victim ignores the notification sent to their inbox (for example, mistaking it for spam). Next, the attacker waits for the victim to try to create an account on that site themselves, or tricks them into doing so.
As a result, the attacker can carry out five different types of attacks:
- Classic-federated merge (CFM): The vulnerable platform supports account merging, and when the victim creates an account with an existing email address, sometimes the platform doesn’t even notify them. The attack is based on offering the victim a Single-Sign-On (SSO) option, so the victim never changes the password set by the attacker.
- Unexpired session (US): After creating the account, the hacker keeps the session active using an automated script. When the victim creates an account and resets the password, the active session may not be invalidated, so the attacker retains access.
- Trojan identifier (TID): Combines the Classic-Federated Merge and Unexpired Session attacks. The attacker creates a pre-hijacked account using the victim’s email, then links it to the attacker’s Identity Provider (IdP) account for federated authentication. When the victim resets the password (as in the US attack), the attacker still has access via federated authentication.
- Unexpired email change (UEC): The attacker creates an account using the victim’s email, then requests an email change but doesn’t confirm it. After the victim resets the password, the attacker confirms the change and takes over the account.
- Non-verifying IdP (NV): The hacker exploits the lack of IdP ownership verification when creating an account, opening up abuse opportunities with cloud login services like Okta and Onelogin.
Why Are Services Vulnerable?
Since many services now require new users to confirm that an email address belongs to them, creating new accounts with someone else’s email often won’t work. To bypass this, an attacker can create an account with their own email and then change it to the victim’s email, abusing standard functionality available on most online services.
The researchers note that the most common issue is the unexpired session (US) problem. Notable large and vulnerable platforms include Dropbox (UEC), Instagram* (TID), LinkedIn (US), WordPress.com (US and UEC), and Zoom (CFM and NV). The experts reported all discovered issues to the companies involved, many of which have since fixed the vulnerabilities and classified them as high severity.
How to Protect Yourself
Unfortunately, the experts point out that they only studied a few major platforms, and similar problems can be found on thousands of other sites. The drive to minimize registration friction on online platforms often comes at the expense of account security.
To reduce the risks of such attacks, specialists recommend that users immediately enable multi-factor authentication (MFA) for their accounts, which should also invalidate all previous sessions.
* Instagram is blocked in Russia and belongs to Meta, which is recognized as an extremist organization and banned in the Russian Federation.