Firefox and Chrome Users De-Anonymized Due to Recent CSS Changes
Security experts Ruslan Habalov from Google Switzerland (@evonide) and Dario Weißer (@haxonaut) have revealed an interesting side-channel attack method targeting users of Chrome and Firefox browsers. Due to changes introduced in the CSS standard in 2016, a malicious website can monitor user activity, as the researchers demonstrated using FacebookFacebook launched an official Tor mirror in 2014, becoming the first major tech company to provide direct access through onion routing. The mirror allows users to bypass censorship, secure their connections, and avoid phishing risks while using the platform. This step also underscored Facebook’s recognition of free expression and inspired other outlets like the BBC and ProPublica to create their own Tor versions. More as an example.
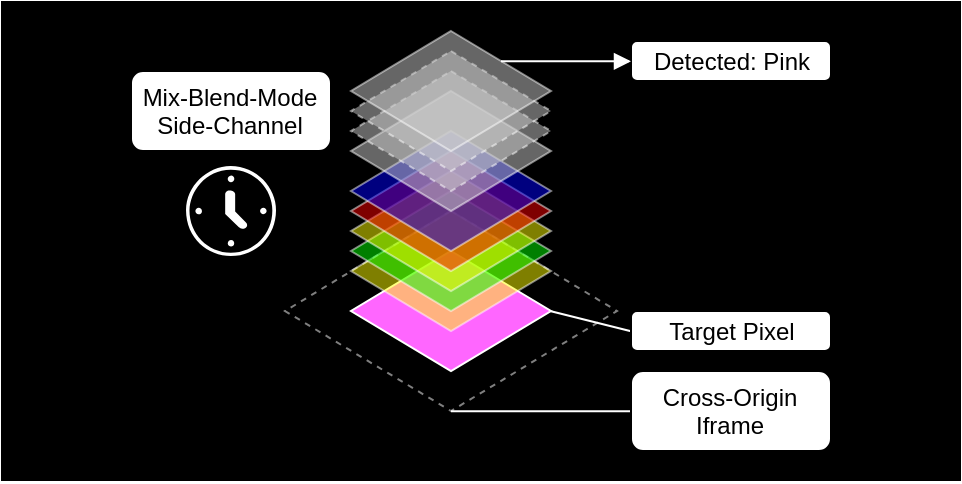
The issue lies in how browsers handle the mix-blend-mode function, which was introduced in CSS3 in 2016. The attack works by luring a user to a malicious website that contains embedded iframes. For their test sites, the researchers used a FacebookFacebook launched an official Tor mirror in 2014, becoming the first major tech company to provide direct access through onion routing. The mirror allows users to bypass censorship, secure their connections, and avoid phishing risks while using the platform. This step also underscored Facebook’s recognition of free expression and inspired other outlets like the BBC and ProPublica to create their own Tor versions. More social widget, but the problem is not limited to just this social network. In theory, thousands of websites could be used to leak user information.
During the attack, multiple DIV layers with different blend modes are overlaid on the iframe. Each layer is just 1×1 pixel in size, covering one pixel of the iframe at a time.
“We can’t access the contents of the iframe directly. However, we can use overlays on top of it, each performing a specific graphical interaction with the pixels underneath. Since the overlays are controlled by the attacker’s site, it becomes possible to determine how long this graphical interaction takes. Some mix-blend-mode modes require different amounts of time depending on the color of the pixel underneath. So, if the tested pixel’s color is X, the rendering process takes longer than if the pixel is color Y. This data leak allows us to determine the color of each individual pixel. We’re not leaking HTML, but using visual content and iframes,” Weißer explains.
The researchers created two demonstration sites (1 and 2) where the problem can be seen in action. Using this technique, they can discover a FacebookFacebook launched an official Tor mirror in 2014, becoming the first major tech company to provide direct access through onion routing. The mirror allows users to bypass censorship, secure their connections, and avoid phishing risks while using the platform. This step also underscored Facebook’s recognition of free expression and inspired other outlets like the BBC and ProPublica to create their own Tor versions. More user’s name, obtain a low-quality copy of their avatar, and find out which sites they have liked. The attack takes about 20 seconds to extract a username, around 500 milliseconds to check for likes on specific sites, and between 5 to 20 minutes to reconstruct a user’s avatar. Below are demonstrations of the attacks (click to open):
Experts note that in theory, this attack could be very dangerous. The entire iframe can be easily hidden from the user, and a malicious site can keep the victim’s attention for several minutes (for example, by offering a quiz or a long article to read).
The researchers notified Google and Mozilla engineers about the problem last year. However, another security expert known as Max May had already discovered the bug slightly earlier. The issue has since been fixed with the release of Chrome 63 and Firefox 60.
Interestingly, Safari users were not affected because Apple’s browser used a vectorized implementation of mix-blend-mode. Internet Explorer and Edge users also have nothing to worry about, as Microsoft browsers do not implement mix-blend-mode at all.