Maximum Security OS: Choosing a Distribution for Bypassing Blocks and Protecting Against Surveillance
If you’ve ever used the Tails distribution—or even run it daily—you know it’s not the only operating system that can hide your presence online and help bypass regional restrictions. In this article, we’ll explore five Tails competitors, each with its own unique features for privacy and anonymity.
Key Elements of Privacy
Experienced Linux hackers can build a custom OS tailored to their needs, packed with favorite tools and encrypted to the core. But this takes a lot of time and is only practical for the most dedicated users. For everyone else, there are ready-made options with thousands of privacy details already considered and tested protection tools pre-installed.
Despite their differences, these distributions share many common features, as privacy is built on similar principles. Key privacy measures include:
- Guaranteed removal of session traces and unique (potentially compromising) data used during a session
- Encryption of data that needs to be saved (wallets, documents, media, configs, etc.)
- Hiding the very fact of storing encrypted data (using steganography and masking among decoy containers)
- Application isolation and running some services in separate virtual machines (sandboxing, Xen, VirtualBox, etc.) to reduce deanonymization risk if infected
- Kernel patches for enhanced process interaction control and minimizing exploit-based deanonymization
- Emergency OS shutdown tools with rapid deletion of compromising data in case of physical seizure
- Early MAC address spoofing (usually at boot)
- Preventing IP address leaks (VPN monitoring, anti-DNS leak, script filtering, proxy chains, Tor routing, etc.)
- Anonymous communication channels (chats, email, file sharing)
- Bypassing regional blocks (auto-setup of public DNS, free VPNs, fast proxies, Tor, I2P, Freenet)
No single distribution offers all these features at once, nor is it necessary—many functions overlap or are mutually exclusive.
Kodachi
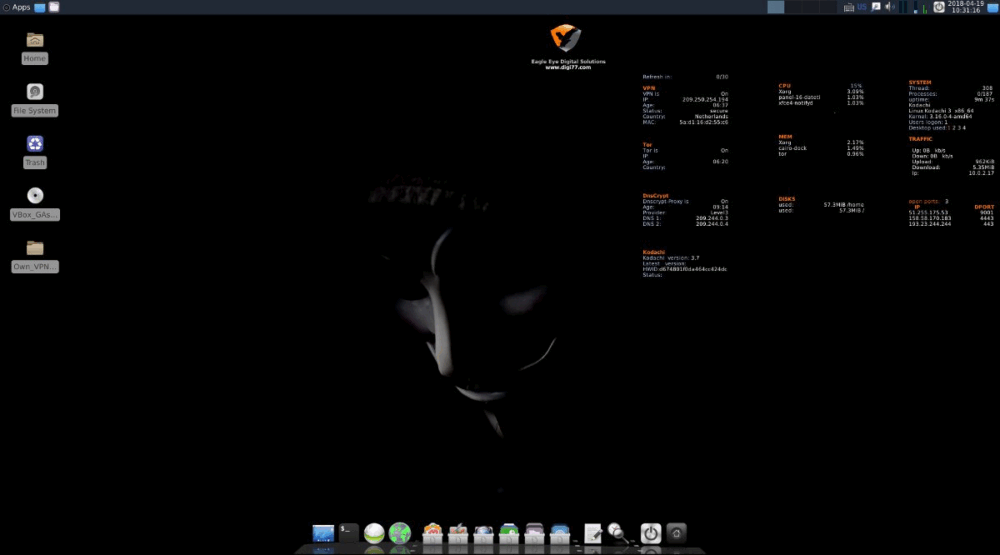
Kodachi is an anti-forensic Debian-based distribution focused on privacy, making forensic analysis of your drives and RAM difficult. The latest stable version, Kodachi 3.7, was released in January 2017 and originates from Oman—a country familiar with internet censorship.
Kodachi uses the Xfce desktop, styled to resemble macOS. Real-time status of Tor and VPN connections, as well as system parameters, are displayed right on the desktop.
- All traffic is forced through Tor and a pre-configured free VPN.
- DNScrypt is integrated to encrypt DNS queries, preventing DNS leaks and hiding activity from ISPs.
- Multi Tor allows quick switching of exit nodes by country, and PeerGuardian hides your IP in P2P networks and blocks blacklisted nodes.
- Uncomplicated Firewall (ufw) with a GUI is used as a firewall.
- Firejail sandboxing is built-in for isolating apps, especially browsers, email, and messengers.
- Pre-installed cryptography tools: TrueCrypt, VeraCrypt, KeePass, GnuPG, Enigmail, Seahorse, and more.
- Forensic countermeasures: RAM is overwritten with random data on shutdown to prevent cold boot attacks.
- Panic Room: quick-access tools for wiping disks and RAM, restarting network connections, locking the screen, or even destroying the OS.
Kodachi runs as a typical Live USB but can also be used in a virtual machine. Default login: username kodachi, password r@@t00. For sudo: username root, password r@@t00.
MOFO Linux
MOFO Linux is a fast-evolving, feature-rich Ubuntu-based OS. Out of the box, it offers SoftEther VPN and OpenVPN with automatic selection of the 15 fastest free servers, showing their ping and bandwidth.
- Supports Tor, VPN, I2P, Lantern, and Psiphon (though Psiphon may be buggy and Lantern’s free tier is limited to 500MB/month).
- Freenet client can be installed in a couple of clicks for access to uncensorable sites and forums.
- IPFS (Interplanetary File System) support for sharing files and creating censorship-resistant sites.
- Cjdns protocol for creating encrypted IPv6 networks.
- eCryptfs provides on-the-fly encryption over existing filesystems (ext3, ext4, XFS) without needing a special partition.
- ZuluCrypt utility supports TrueCrypt and VeraCrypt containers.
As of testing, version mofolinux-6.0 (Feb 18, 2018) was available. No default admin password is set.
Subgraph OS
Subgraph OS is a Debian fork praised by Edward Snowden for its concept, though its implementation is still rough. The latest version is the September 2017 alpha, which can run live but is intended for full installation.
- Key feature: Oz sandboxing system isolates selected apps using namespaces and seccomp-bpf, similar to Firejail.
- Kernel is patched with PaX/Grsecurity for enhanced security (ASLR, non-executable stack, strict chroot isolation, etc.).
- Installs on an encrypted partition, controls app network access, and supports YubiKey hardware keys.
- All outgoing connections are routed through Tor by default.
- Integrated instant messenger (fork of CoyIM) and OnionShareOnionShare is an open-source tool that lets people share files, host websites, and even chat securely through the Tor network. Instead of relying on cloud services, it creates a temporary onion address directly from your computer, ensuring anonymity and direct peer-to-peer transfers. Once the app closes, the link expires, making it ideal for one-time, private exchanges. While slower than traditional services, OnionShare is a vital tool for journalists, activists, and anyone who values privacy over convenience. More for anonymous file sharing.
However, only certain apps run in the sandbox; others, including the GNOME desktop, do not. This opens potential attack vectors, as demonstrated by a public hack in April 2017. For example, Tor Browser can write files to ~/Downloads, and if a malicious script is saved there, it could be executed by the unsandboxed file manager.
heads
heads (lowercase by design) is a relatively new OS based on Devuan (a Debian fork using SysVinit instead of systemd). As of March 26, 2018, version 0.4 was available. It supports only i386 and x86_64 architectures, so it’s not suitable for ARM-based mobile devices.
- Uses the lightweight Awesome window manager (with Openbox as an alternative).
- Minimal set of utilities: browser, email, chat, crypto wallet, and a few file tools.
- Deep Tor integration: all traffic (not just browser) goes through Tor. The heads website is also available via Tor.
- Can spoof MAC address at startup; Permakey kernel module shuts down the OS if the boot USB is removed (can be disabled at startup).
- External drives are not auto-mounted; in Openbox, mount via the udiskie icon.
heads is still in early development, so expect issues with hardware drivers and other bugs. If your hardware is compatible, it boots quickly in Live mode and routes all app traffic through Tor. However, this can cause problems with some services (e.g., many IRC channels block Tor exit nodes).
Tails
Tails (The Amnesiac Incognito Live System) is probably the most well-known OS for anonymous web surfing and bypassing internet censorship. The latest version at the time of this review was 3.6.2 (April 11, 2018).
- Based on Debian Stable with GNOME desktop; supports Russian and other languages.
- Configures Tor and spoofs MAC address at startup.
- Tor setup takes a few minutes and is monitored via Onion Circuits.
- Regular security updates; vulnerabilities are patched quickly.
- Detects if running in a VM and warns that anonymity cannot be guaranteed in that case.
- Pre-installed software is moderate in size; you can install more from Debian repos, but changes are lost after reboot unless you create an encrypted persistent volume.
- All data is stored in RAM and wiped on shutdown to prevent cold boot attacks. MAC address randomization and protection against sudden USB removal are included. All traffic, including DNS, goes through Tor.
- Gobby is integrated for real-time anonymous collaboration, supporting syntax highlighting and multi-user editing.
Despite its maturity, Tails still has occasional bugs, such as apps crashing or disappearing search results in Liferea. These are intermittent and not always reproducible.
Whonix
Whonix is the most unique OS in this review. It comes as two pre-configured virtual machines (.ova): Whonix-Gateway (server) and Whonix Workstation (client). The latest stable release was May 31, 2016. Default login: username user, password changeme.
- Import both VMs into VirtualBox and start Gateway first. Minimal resources required; optimal settings are pre-set.
- Setup is guided by a wizard—no command line needed.
- Gateway handles Tor/VPN routing, DNS, and packet filtering. Workstation is isolated from the network except through Gateway.
- This separation protects your real IP and data even if Gateway is compromised.
- Pre-installed apps: Tor Browser, Tor Messenger, Tox, Ricochet, Thunderbird, TorBirdy (PGP support), secure file transfer via SCP, and more.
- Whonix can run on Windows, macOS, or Linux hosts, but its security depends on the host OS.
- For maximum security, run Whonix inside Qubes OS on trusted hardware.
Conclusion
Among distributions for anonymous web surfing and bypassing censorship, some are well-known (Tails, Subgraph OS) but not always user-friendly, while lesser-known options (MOFO, Kodachi) can be more functional. These latter options are worth considering when choosing a Live OS.
This review does not cover distributions that have been inactive for over two years, such as JonDo, Sabayon Linux, TENS (endorsed by the NSA), Discreete Linux, IprediaOS, and others. This doesn’t mean they’re bad—just that more up-to-date options are now available, and almost everyone has tried making their own anonymous Linux fork by now.