Hardware Backdoors Can Cost as Little as $200
Software hacking no longer surprises anyone—people have more or less learned how to deal with it. Unfortunately, the possibility of hardware hacking has now been definitively proven as well. The complexity and cost of such an operation are surprisingly low, making it accessible to anyone skilled with a soldering iron and a programmer.
Rumors about “backdoors” and hardware implants in computer equipment have circulated for years. While not all of these stories are grounded in reality, some remote management mechanisms do have vulnerabilities that experienced attackers can exploit.
In 2018, a scandal erupted when Bloomberg reported that Supermicro motherboards might contain a tiny chip not specified in the official documentation. This alleged “modification” supposedly affected about 30 companies. However, all the “victims” denied finding any extra chips in their equipment, and Supermicro even conducted an independent investigation. Nevertheless, the U.S. government believes such attacks could be the work of the Chinese military.
Sepio Systems, a company specializing in hardware security, has previously confirmed that such hardware implants are possible and that their experts have encountered them before. For example, they described a case involving a Supermicro server where a malicious chip was embedded in the traces leading to the Ethernet port. Its activity was detected through unusual network traffic, but the specialists were unable to fully determine what data the device was transmitting or processing.
Hardware Backdoors: Myth or Reality?
So how much does such a hardware modification cost, and can it be done by someone other than intelligence agencies or organizations with virtually unlimited resources? Enthusiasts have thoroughly tested all possible methods and proven that this operation is indeed possible. Researcher Monta Elkins promised to provide a detailed description of this type of attack at the CS3sthlm conference, held from October 21 to 24 in Stockholm.
Elkins claims that the process is not overly complicated and doesn’t require any special skills—any sufficiently motivated attacker, whether a spy, hacker, or criminal, can easily modify a server or network device as needed. For an experienced hacker comfortable with both software and soldering, the operation costs only about $200, including equipment expenses.

Specifically, a soldering heat gun costs about $150, a microscope about $40, and the chips used for hacking can be as cheap as $2 each. The researcher managed to modify a Cisco firewall in such a way that, in his opinion, most system administrators would not notice the hack.
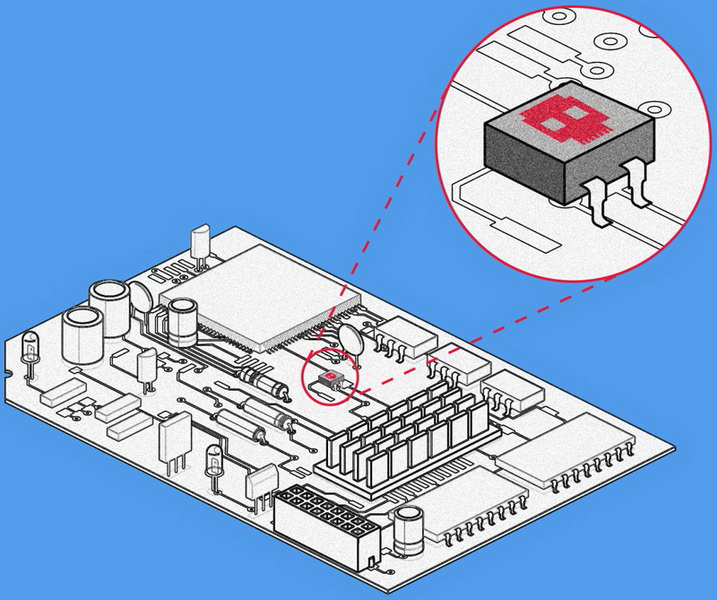
For the chip, Elkins chose the 8-bit Atmel ATtiny85 microcontroller from a Digispark Arduino board. While not as tiny as the “grain of rice” described in the Bloomberg article, its SOIC-8 package measures just 4 × 5 mm. Running at 16.5 MHz, the controller is quite powerful for its size.
The researcher selected a spot on the Cisco ASA 5505 motherboard that didn’t require extra wiring and installed the chip there, pre-flashing it with the necessary firmware. Elkins claims that similar modifications are possible for other Cisco devices as well. The company responded: “If new information emerges that our customers need to know, we will communicate it through our usual channels.”

As shown in the photo, spotting the extra microchip isn’t easy, even on a relatively small and simple motherboard. If the soldering is done carefully, the chip looks factory-installed and doesn’t attract attention. Elkins notes that even more covert installations are possible, as well as the use of even smaller chips. He chose the ATtiny85 simply because it’s easy to program.
The controller is soldered to the serial port pins. After the device is powered on, the chip waits for the firewall OS to load, then mimics human actions. It initiates a password recovery procedure, creates a new administrator account, and thus gains access to all device settings. What happens next depends on the attacker’s intentions: they could gain full remote access, disable all security settings, access network logs, and more.

Another researcher, Trammell Hudson, also confirmed the possibility of hardware hacking. He recreated the Supermicro scenario and connected to the BMC controller, which, among other things, manages remote system access. As the “malicious” component, Hudson used a tiny FPGA measuring just 2.5 mm², replacing one of the resistors on the motherboard—most likely a Lattice XO2-1200 chip.
Thus, the possibility of hardware hacking for various IT equipment is now fully proven and confirmed. The most dangerous aspect is that almost any sufficiently skilled enthusiast can exploit this vulnerability, even without significant financial resources. In the coming years, cybersecurity companies will have a lot of work to do. Even experienced users are advised to carefully inspect their devices for any “extra” chips.