Using Bitcoin Transaction Analysis to Deanonymize Tor Hidden Service Users
Online anonymity has never been a more pressing issue than it is today. To achieve bulletproof privacy, internet users around the world are turning to various solutions (such as VPNs, SOCKS proxies, I2P, etc.), with the Tor network being the most popular. Tor is a vibrant anonymous network with millions of users. Bitcoin remains the preferred payment method on Tor and other darknet platforms, even though its privacy and anonymity features are far from perfect. Today, the reliance on Bitcoin as the main payment method significantly undermines the anonymity of both Tor users and the operators of hidden services.
But Isn’t Bitcoin Anonymous?
Although several studies have shown that Bitcoin transactions are not truly anonymous, Bitcoin is still the most widely used currency on the deep web. Researchers have recently demonstrated that even when Bitcoin is used within decentralized networks like Tor, users are still vulnerable to deanonymization and “man-in-the-middle” attacks, especially at the network level.
Users of Tor hidden services are a special category of Bitcoin users who are highly concerned about their anonymity, mainly because both users and operators rely on Tor to conceal potentially illegal activities. However, both groups become vulnerable to deanonymization as soon as their Bitcoin addresses are exposed. By analyzing transactions sent to and from these addresses, a significant amount of information can be gathered and used to infer confidential details about Tor hidden services and their users, potentially linking a user to a specific hidden service.
A recently published scientific study highlighted how combining publicly available data from various social networks (such as Twitter, Bitcointalk.org, FacebookFacebook launched an official Tor mirror in 2014, becoming the first major tech company to provide direct access through onion routing. The mirror allows users to bypass censorship, secure their connections, and avoid phishing risks while using the platform. This step also underscored Facebook’s recognition of free expression and inspired other outlets like the BBC and ProPublica to create their own Tor versions. More, etc.), the Bitcoin network, and data from Tor hidden services can lead to leaks of confidential information, resulting in the deanonymization of Tor users.
How Is This Possible?
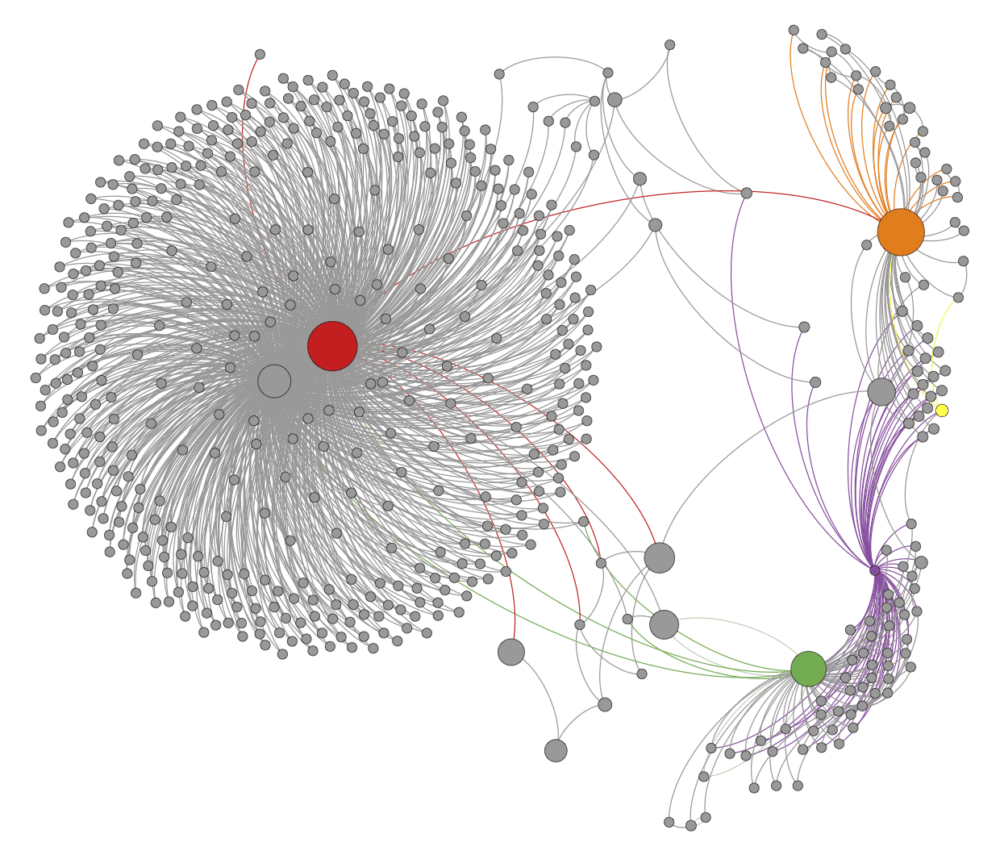
By examining the landing pages of various Tor hidden services, researchers found it was relatively easy to obtain the Bitcoin address for each service. They used custom software to analyze 1,500 pages from different Tor hidden services and compiled a list of 105 Bitcoin addresses controlled by these services, along with several addresses linked to buyers. Researchers also collected Bitcoin addresses from Twitter and Bitcointalk, where they are often posted publicly. About 5 billion tweets and 1 million forum pages were analyzed, revealing 4,200 and 41,000 online identities, respectively.
The transactions of these collected Bitcoin addresses were analyzed to link Bitcoin users—whose identities were identified through their social media profiles—to hidden services on Tor. This led to successfully connecting some identities to specific Tor hidden services and accessing their complete transaction histories, since all transactions are transparent on the blockchain.
Using a simple heuristic approach, the researchers enhanced their transaction analysis with a “wallet closure” technique to expand the set of Bitcoin addresses associated with a single user. For each Bitcoin address in their list, they were able to discover other addresses controlled by the same user. As a result, they increased the number of detected links between users and various Tor hidden services, raising the number of successfully deanonymized users.
The study identified 81 users of hidden services (such as Wikileaks and The Pirate Bay). The wallet closure analysis increased the number of deanonymized users to 125. In the case of The Pirate Bay, researchers were even able to determine the exact age and geolocation of some users.
Another case study revealed users of different ages and from various parts of the world who had links to Silk Road (Ross Ulbricht’s marketplace) Bitcoin addresses. Interestingly, one of these users was just 13 years old and used multiple social media accounts that revealed his real identity!
The research also uncovered thousands of wallets servicing Wikileaks, The Pirate Bay, and various Silk Road offshoots. Typically, these are transit wallets—funds don’t stay in them but are quickly distributed to other wallets.