Man-in-the-Middle: Explained in Simple Terms
In this article, we’ll break down what a “man-in-the-middle” (MITM) attack is—one of the classic methods for stealing data and controlling internet traffic.
How the Internet Works: The Basics
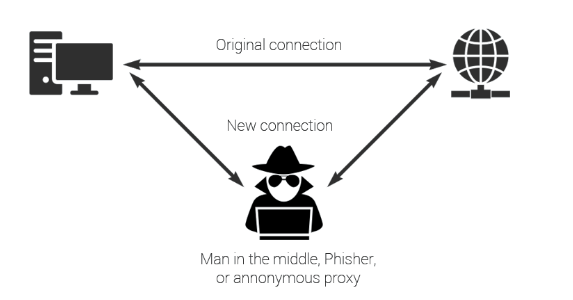
To understand how a MITM attack works, it’s important to first know how the internet operates at a basic level. There are three main types of devices involved: clients, routers, and servers. The most common protocol for client-server communication is HTTP. Most web pages, email, instant messaging, and similar services use this protocol.
When you enter a website in your browser, your device (the client) sends a request to a web server. The HTTP packet travels through several routers to reach the server. The server then sends the web page back, which your browser displays. For secure communication, it’s crucial that HTTP messages are transmitted safely to ensure privacy and confidentiality.
What Makes a Secure Communication Protocol?
A secure communication protocol should have the following properties:
- Confidentiality – Only the intended recipient can read the message.
- Authenticity – The parties involved are who they claim to be.
- Integrity – The message hasn’t been altered during transmission.
If any of these are missing, the protocol fails to provide security.
How Man-in-the-Middle Attacks Work Over HTTP
In computer networks, an attacker can position themselves between you and the server using a method called ARP spoofing. For example, someone on your Wi-Fi network can send you fake ARP packets, causing your device to unknowingly route all your traffic through a router controlled by the attacker. The attacker can then sniff, modify, or even block your traffic. Usually, they’ll set up a port to forward your requests so you don’t notice anything is wrong.
To prevent such attacks, a secure version of HTTP was created. Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), are cryptographic protocols that secure data transmission over networks. These are often referred to as SSL, and when HTTP uses SSL, it’s called HTTPS (note the “S” at the end).
SSL-based attacks are much harder to pull off. Modern SSL uses strong encryption, but if anything is set up incorrectly, an attacker can still intercept your traffic. For example, if an attacker removes the “S” from your requested URL, your browser may connect over insecure HTTP instead of HTTPS, making your data vulnerable.
You can spot this if you request https://login.yahoo.com/ but get redirected to http://login.yahoo.com/. This is a red flag. To prevent this, servers can enforce strict HTTPS connections using protocols like HSTS, which force all connections to use SSL. If an attacker tries to downgrade the connection, the server simply won’t respond.
However, even this method isn’t foolproof. An attacker could establish an SSL connection to the server but relay it to you over HTTP. Modern browsers like Chrome, Firefox, and Tor track sites that use HSTS and SSL to help prevent these attacks. For a successful MITM attack, the attacker would need to create an SSL connection for the victim, which is difficult without access to the victim’s browser.
Understanding the SSL Protocol
Let’s look at SSL from a hacker’s perspective. Breaking any communication protocol comes down to attacking one of the three properties: confidentiality, integrity, or authenticity.
SSL uses asymmetric encryption, unlike symmetric encryption. In symmetric encryption, the same key is used for both encrypting and decrypting data, which is risky because an attacker could steal the key during the initial exchange. Asymmetric encryption uses two keys for each participant: a public key for encryption and a private key for decryption. Anyone can use your public key to send you encrypted messages, but only you can decrypt them with your private key.
SSL ensures:
- Confidentiality – Asymmetric cryptography keeps data private.
- Integrity – Strong encryption makes it hard for attackers to alter messages undetected.
- Authenticity – The server proves its identity by sending an SSL certificate signed by a trusted certificate authority (CA).
If an attacker somehow obtains a valid certificate, they can perform a MITM attack by creating two SSL connections: one with the server and one with the victim. The server thinks it’s talking to a regular client, and the victim can’t tell the difference because the attacker presents a valid certificate. The attacker can then read and manipulate all data passing through their system.
The most effective attacks involve manipulating certificates. If an attacker compromises the victim’s browser, they can install a self-signed certificate that the browser trusts by default. In other cases, attackers may forge certificates themselves.
Certificate Issues
Server certificates are issued and signed by special organizations called certificate authorities (CAs). Every browser has a list of trusted CAs, and you can add or remove them. If you remove a major CA, you won’t be able to access most sites that use its certificates, and your browser will warn you about potential attacks.
Certificates and CAs have always been a weak link in HTTPS security. Even if every CA only issued certificates to verified servers, it’s still hard to trust so many unknown organizations. Today, over 650 organizations can issue certificates, which raises concerns about security. If any of them are compromised, attackers can issue certificates for any site they want.
Even when there was only one major CA (VeriSign), problems arose—those trusted to protect us sometimes sold interception services. Many certificates have been created through hacking at various levels, and countless vulnerabilities have been exploited to trick users into trusting fake certificates. If you’re interested in this topic, there’s plenty of information online for deeper study.
Network Forensics: Detecting MITM Attacks
Since attackers send fake ARP packets, you won’t see their IP address, but you can check the MAC address, which is unique to each network device. If you know your router’s MAC address, compare it to your default gateway’s MAC address to see if you’re really connected to your router or to an attacker’s device.
On Windows, use the ipconfig command in the command prompt to see your default gateway’s IP address. Then use arp –a to view the MAC address of your gateway. If you don’t know your router’s MAC address, you can still spot an attack by monitoring network activity with tools like Wireshark. If you suspect you’re being targeted, set up an automated tool to alert you if your gateway’s MAC address changes.
Note: A skilled attacker can spoof the MAC address, making detection much harder.
Conclusion
SSL is a strong protocol because it forces attackers to do a lot of work to intercept your confidential data. However, it can’t fully protect you from government hackers or highly skilled organizations.
As a regular user concerned about privacy, you should protect your browser and personal computer to prevent fake certificates from being installed. Review your list of trusted certificate authorities and remove any you don’t personally trust.