42,000 Fake Brand Websites Drive Ad Traffic and Spread Malware
A Chinese group known as Fangxiao has created a massive network of 42,000 websites that impersonate well-known brands—including Coca-Cola, McDonald’s, Knorr, Unilever, Shopee, and Emirates. These sites redirect visitors to pages promoting adware apps, dating sites, “free” giveaways, or infect their systems with the Triada trojan.
According to experts at Cyjax, Fangxiao has been active since at least 2017 and is believed to be based in China, as indicated by the use of the Chinese language in their control panels. In a recently discovered campaign, the scammers have spoofed more than 400 well-known brands across retail, banking, travel, pharmaceuticals, transportation, finance, and energy sectors.
How the Scam Works
To generate the necessary traffic for their clients and their own sites, Fangxiao members register about 300 new domains every day. Since March 2022, the attackers have used at least 24,000 domains to promote fake prize giveaways and surveys to their victims.
Most of these fraudulent sites are registered in the .top domain zone, followed by .cn, .cyu, .xyz, .work, and .tech. The scammers’ resources are always hidden behind Cloudflare and registered through GoDaddy, Namecheap, and Wix.
How Victims Are Targeted
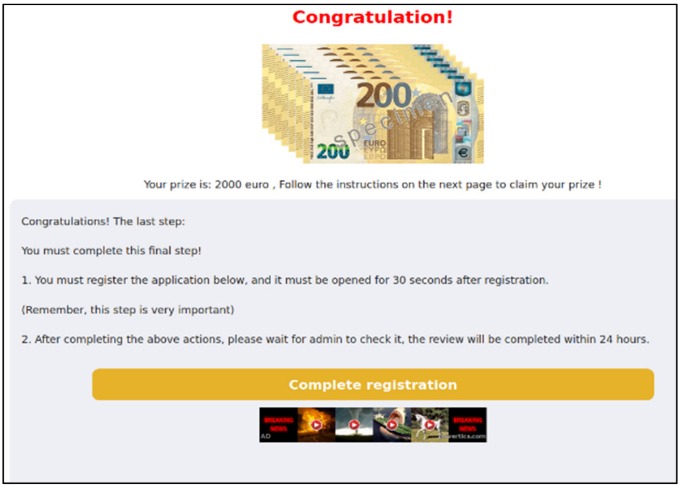
Users typically land on these sites via mobile ads or after receiving a WhatsApp message claiming they have a special offer or prize waiting for them. The message includes a link, and clicking it takes the victim to a landing page that redirects them to a survey site, which they are told must be completed within a certain time frame.
Redirection Scheme
In some cases, completing the survey leads to the download of an app, which the victim is instructed to open and keep running for at least thirty seconds—likely enough time to register a new user via referral. The landing pages also display ylliX ads, which Google flags as “suspicious.” Clicking these ads triggers a separate chain of redirects.
The redirection process depends on the user’s location (IP address) and user agent, and typically leads to one of the following:
- Downloading the Triada trojan
- Redirecting to Amazon via an affiliate link
- Fake dating sites
- SMS micro-payment scams
Malicious Apps and Adware
Another destination in the Fangxiao campaign is the Google Play Store page for the app “App Booster Lite — RAM Booster.” This app is described as a performance booster for Android devices and has over 10 million downloads. While analysts say the app does not contain malicious features, it requests dangerous permissions and displays a large number of ads, with pop-ups that are difficult to close. The publisher, LocoMind, shares an IP address with another developer, Holacode, previously linked to adware distribution.