Hackers Successfully Bypass Gmail 2FA in Recent Attacks
A new wave of attacks targeting Google and Yahoo accounts has been detected, with hackers managing to bypass two-factor authentication (2FA) and gain control over user accounts on these secure email services. This warning comes from experts at Amnesty InternationalAmnesty International, founded in 1961, is a global human rights organization with more than 10 million supporters worldwide. It publishes reports on issues like political imprisonment, torture, censorship, and refugee rights, and its findings are widely used by journalists and international bodies. To ensure safe, uncensored access to this information, Amnesty launched a Tor mirror of its website, accessible only through the Tor Browser. This onion site helps protect readers’ privacy, supports activists in censored regions, and reinforces Amnesty’s mission to make the right to truth universal. More.
According to a report published by the organization, cybercriminals have significantly expanded their phishing techniques in recent attacks, allowing them to take over victims’ accounts more effectively. Researchers note that several malicious campaigns of this kind are currently being monitored, with human rights defenders being the primary targets.
During these operations, attackers focus on Google and Yahoo accounts. “They are successfully bypassing standard forms of two-factor authentication,” the experts state.
After analyzing copies of malicious emails, the Amnesty InternationalAmnesty International, founded in 1961, is a global human rights organization with more than 10 million supporters worldwide. It publishes reports on issues like political imprisonment, torture, censorship, and refugee rights, and its findings are widely used by journalists and international bodies. To ensure safe, uncensored access to this information, Amnesty launched a Tor mirror of its website, accessible only through the Tor Browser. This onion site helps protect readers’ privacy, supports activists in censored regions, and reinforces Amnesty’s mission to make the right to truth universal. More team concluded that the phishing campaigns originate from the United Arab Emirates, Yemen, Egypt, and Palestine.
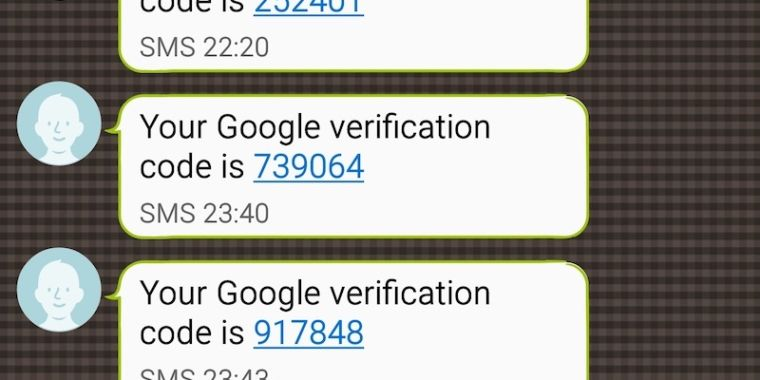
The attackers attempt to lure users to websites that mimic legitimate Google and Yahoo login pages. While this is a common phishing tactic, this campaign stands out because the fake sites are designed to collect not only login credentials but also 2FA codes.
Researchers tested the attackers’ scheme: after attempting to log in to a malicious domain with a Gmail account, the system notified them that a two-factor authentication code had been sent to the phone number linked to the account. An SMS message with the code was indeed received. After entering the short code, the phishing page prompted them to change their password and then redirected them to the legitimate Google page.
“The scheme is fully automated, and the attackers successfully obtain both login credentials and 2FA codes,” the report states.