Firefox to Conduct DNS-over-HTTPS Experiment
Mozilla developers have announced a new study as part of their preparations to implement DNS-over-HTTPS (DoH) in Firefox. During this experiment, statistics will be collected from some U.S. Firefox release users regarding the use of parental control systems and corporate DNS resolvers. Participation in the experiment is optional and can be declined via the “about:studies” page, where the study appears as “Detection Logic for DNS-over-HTTPS.”
What Data Will Be Collected?
The study will gather only anonymized data, consisting of counters without any specific addresses or domain names. To detect parental control systems, Firefox will send a request to resolve the domain exampleadultsite.com. If the returned IP does not match the actual IP, it will be considered an indication that DNS-level adult content blocking is active. Additionally, the IP addresses returned for Google and YouTube will be checked to see if they are being redirected to restrict.youtube.com, forcesafesearch.google.com, or restrictmoderate.youtube.com.
To identify the use of internal corporate resolvers, Firefox will check if the hosts determined when opening websites use unusual top-level domains (TLDs) and if intranet addresses are returned for them.
Why Is This Experiment Being Conducted?
The motivation behind this experiment is concern that enabling DNS-over-HTTPS by default could disrupt existing DNS-based parental control systems and create issues for users in corporate networks. Many organizations use DNS servers that provide information about internal domains not visible on the public internet.
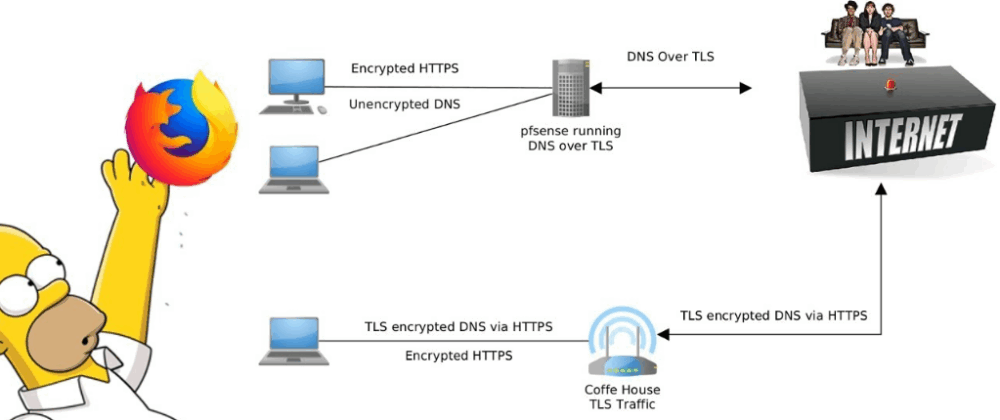
Benefits and Technical Details of DoH
DoH can help prevent leaks of requested hostnames through ISP DNS servers, protect against man-in-the-middle (MITM) attacks and DNS traffic tampering, bypass DNS-level blocks, and enable DNS resolution when direct access to DNS servers is not possible (such as when using a proxy). Normally, DNS queries are sent directly to the DNS servers specified in the system configuration. With DoH, the IP address request is encapsulated in HTTPS traffic and sent to an HTTP server, where the resolver processes requests via a Web API. The existing DNSSEC standard only encrypts authentication between client and server, but does not protect traffic from interception or guarantee the confidentiality of queries.
How to Enable or Configure DoH in Firefox
To enable DoH in Firefox, go to about:config and change the value of the network.trr.mode variable (supported since Firefox 60):
- 0 – DoH is completely disabled
- 1 – Use DNS or DoH, whichever is faster
- 2 – Use DoH by default, DNS as a fallback
- 3 – Use only DoH
- 4 – Mirror mode: DoH and DNS are used in parallel
By default, Firefox uses Cloudflare’s DNS server, but you can change this via the network.trr.uri parameter. For example, you can set it to https://dns.google.com/experimental or https://9.9.9.9/dns-query.