Undocumented Apple Hardware Feature Used in Operation Triangulation Attacks
Experts from Kaspersky Lab presented a report titled Operation Triangulation: What You Get When You Attack iPhones of Researchers at the global hacker conference Chaos Communication Congress (37C3). The specialists summarized the results of an extensive investigation and publicly disclosed details about all the vulnerabilities and exploits used in the high-profile attack.
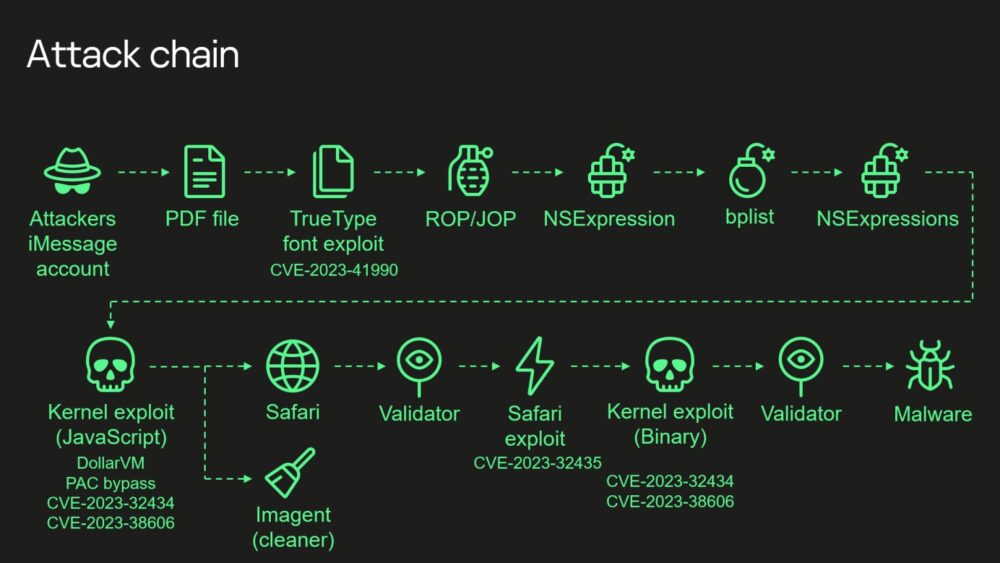
Attack Chain
It was revealed that the espionage attacks targeting iPhones since 2019 exploited undocumented Apple chip features to bypass hardware security protections. The experts described Operation Triangulation as “the most sophisticated attack chain” they have ever seen.
In the summer of 2023, Russia’s FSB and FSO reported a “reconnaissance operation by American intelligence agencies using Apple mobile devices.” Shortly after, Kaspersky Lab published a detailed report on targeted attacks against iOS devices. This campaign was named Operation Triangulation, and according to researchers, the goal was “the stealthy installation of a spyware module on the iPhones of company employees, including both top management and middle managers.” The company reported that these attacks began as early as 2019.
The attacks used a complex exploit delivery method via iMessage that required no user interaction. Previously, experts had already published a detailed report on the TriangleDB malware, written in Objective-C, and explained that the implant was loaded onto devices after attackers gained root access by exploiting a kernel vulnerability in iOS.
Specialists also released a separate report on the stealth techniques and tools hackers used, as well as an analysis of the implant’s activity after compromise. Another report covered five vulnerabilities (including CVE-2023-32434, CVE-2023-32435, CVE-2023-38606, and CVE-2023-41990) involved in these attacks, which Apple rushed to patch.
Analysts say they have nearly completed reverse engineering all aspects of this attack chain and promise to release a series of articles in the new year with detailed descriptions of each vulnerability and its exploitation. However, some aspects of one particular vulnerability remain unclear.
The CVE-2023-38606 Vulnerability
This concerns vulnerability CVE-2023-38606, which was fixed on July 24, 2023, with the release of iOS and iPadOS 16.6. Experts explain that newer iPhone models have additional hardware protection for sensitive kernel memory areas. This protection prevents attackers from gaining full control over the device, even if they have read-write access to kernel memory, as was the case with the CVE-2023-32434 exploit. However, researchers discovered that hackers used another undocumented hardware feature of Apple’s SoC to bypass this protection.
With this feature, attackers could write necessary data to a specific physical address, bypassing hardware memory protection. To do this, they had to write the data, destination address, and data hash into undocumented hardware registers on the chip that are not used by the firmware.
It is believed that this undocumented hardware feature was likely intended for debugging or testing by Apple engineers or at the manufacturing plant, or it may have been included by mistake. Since this feature is inactive in the firmware, researchers admit they “have no idea” how the attackers figured out how to use it, given that there are no instructions for its use.
In the technical part of the report, researchers state that CVE-2023-38606 targets unknown MMIO (memory-mapped I/O) registers in Apple A12-A16 Bionic chips, which turned out to be connected to the GPU coprocessor but were missing from the device tree.
“While analyzing the exploit used in Operation Triangulation, I found that most of the MMIO used to bypass kernel memory hardware protection did not belong to any of the MMIO ranges defined in the device tree. The exploit targets Apple A12-A16 Bionic SoCs and uses undocumented MMIO register blocks located at addresses: 0x206040000, 0x206140000, 0x206150000.
This prompted me to look at the situation from another angle. I examined various device tree files for different devices and firmware versions, but without success. Then I checked the publicly available XNU source code—again, no results. Searching for direct access to these addresses, I looked through kernel images, kernel extensions, iboot, and coprocessor firmware—nothing.
How is it possible that the exploit uses MMIO registers not used by the firmware? How did the attackers learn about them? Which peripheral device(s) do these MMIO addresses belong to?
I had the idea to check which other documented MMIOs are located near these unknown MMIO register blocks. This approach turned out to be successful,”
It is also noted that the exploit authors knew how to use Apple’s proprietary UTT area to wake the processor from sleep mode, even though this is not present in the XNU source code.
Conclusions and Security Implications
In conclusion, the experts summarize that this is an extremely unusual vulnerability, and many questions remain unanswered.
“We do not know how the attackers discovered how to use the undocumented hardware feature or what its original purpose was. We also do not know whether it was developed by Apple or is a third-party component, such as ARM’s CoreSight. But we do know for sure—and this vulnerability proves it—that even the most advanced hardware security measures are powerless against a sophisticated attacker as long as hardware features exist that allow these protections to be bypassed,” the report states.
According to the researchers, manufacturers too often rely on “security through obscurity” when protecting hardware, believing that hardware is much harder to reverse engineer.
“But this is the wrong approach, because sooner or later all secrets come to light. Systems relying on ‘security through obscurity’ will never be truly secure,” the experts conclude.