What Are MTProto Proxies and How Does Telegram Protect Itself from Blocks?
By Anya — May 26, 2018
How Does Telegram Communicate?
Let’s start with the basics. Telegram clients communicate with Telegram servers using their own protocol, MTProto, over TCP. Several server addresses are used, which have remained unchanged for years and are the main connection points. For example, one of the European region addresses is 149.154.167.40. Port 443 is usually used, but this has nothing to do with SSL/TLS.
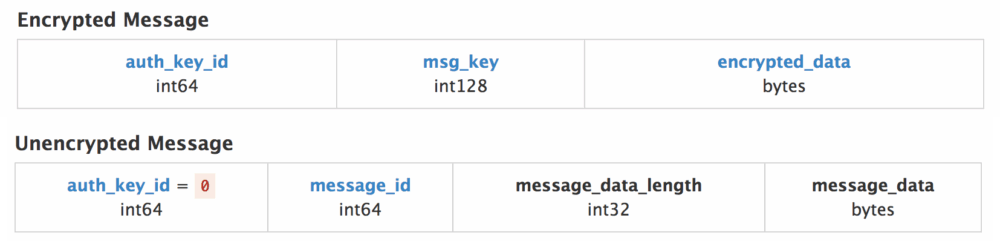
MTProto Packet Format
Each packet consists of several parts. Open packets are only used during the initial communication to exchange keys; after that, all communication is encrypted. Even in encrypted packets, there are constant headers: the first 8 bytes are always the same within a session, as they represent the fingerprint of the authorization key. We’ll come back to this soon.
Government Blocks: The Case of Roskomnadzor
Enter the government and its internet regulator, which starts blocking Telegram! In Russia, this is Roskomnadzor, which adds all Telegram subnets to the blocklist for ISPs, including the one with 149.154.167.40. Providers receive the list and block user access to these addresses.
How Telegram Responds
The Telegram team didn’t leave users stranded. They launched many servers with different hosting providers to accept packets and forward them to the main Telegram servers that were blocked.
How Do Telegram Clients Learn About New Server Addresses?
There are two main methods:
1. DC_UPDATE
This is the first way new server addresses are delivered to user devices. It works only for mobile clients on iOS and Android, using Apple Push Notification Service (APNS) and Google Cloud Messaging (GCM). Telegram sends push notifications containing new addresses. The Telegram app reads them and starts using these addresses for communication.
- Pros: The only way to block this is to block APNS and GCM entirely, which would cut off all notifications for all apps, not just Telegram. Authorities are unlikely to do this.
- Cons: Only works for mobile devices, as desktop OSes lack a unified notification delivery system. It can also be unreliable if the notification doesn’t reach you, especially on iOS where background processing is limited.
Roskomnadzor tracks new addresses delivered via DC_UPDATE and blocks them.
2. Domain Fronting
This method is less well-known. Telegram places an encrypted list of addresses in TXT records of its service domains and on Azure. Clients fetch this data from dns.google.com and tcdnb.azureedge.net/prodv2/config.txt. Domain fronting makes it look like requests are going to google.com or software-download.microsoft.com to bypass filters.
- Pros: Blocking this would require blocking all of
google.comand Windows update services, which is impractical. It works on all platforms, including desktop.
Obfuscated2: Protection Against Advanced DPI
What if the regulator gets smarter? As mentioned earlier, even encrypted Telegram packets have constant headers. ISPs could track these headers and block connections based on packet content, not just server addresses. This would render previous methods useless. However, Telegram implemented protection against such deep packet inspection (DPI) as early as 2017.
Although the MTProto protocol is open and documented, official clients use an extra, undocumented obfuscation layer. The method is described in detail by Tomas Susanka. The client generates a random 32-byte key and a 16-byte Initialization Vector (IV) to encrypt each packet with AES CTR. The key and IV are added to the start of the packet before the encrypted content.
While it may seem pointless to send the decryption key with the packet, this obfuscation makes all packets look like random data. To identify Telegram traffic, ISPs would have to decrypt every suspicious packet using the obfuscated2 method, which is computationally unfeasible for providers.
Connecting to Telegram via Proxy
Despite Telegram’s efforts, temporary servers are quickly blocked, and users lose access again. The next line of defense is up to users: Telegram offers two proxy connection methods in its apps. Both methods keep your messages and data private from proxy server owners, as Telegram traffic is already encrypted and unreadable in transit.
SOCKS5 Proxy
This is a simple but effective method. The Telegram client connects to a SOCKS5 server you specify, which then connects to Telegram servers. Since the SOCKS5 server is outside the blocking country, connections succeed.
- Pros: Fast and easy. Well-known protocol with server implementations for all platforms and OSes.
- Cons: Easily detected by DPI; governments can block SOCKS5 entirely. Login and password are sent in plain text, so never use important passwords. If your Telegram app has cached temporary server IPs, it may try to connect to them via SOCKS5, which can cause issues if the proxy blocks those addresses.
MTProto Proxy
This is what you’ve been waiting for. Any MTProto proxy is a reverse proxy. Unlike SOCKS5, the client communicates with the MTProto proxy as if it’s a Telegram server.
There’s no official documentation for MTProto proxies, but some developers have created their own server implementations by studying client source code. The proxy simply receives packets from the client and forwards them to Telegram servers — but it’s a bit more complex than that.
- The client communicates with the MTProto proxy only using obfuscated2.
- Obfuscated2 is slightly modified here. The key and IV are still sent in the clear, but the packet is encrypted with
sha256(key+secret), wheresecretis a 16-byte parameter you enter when connecting to the proxy. - The
secretis never transmitted during communication. The client uses it to encrypt the packet, and the proxy uses it to decrypt. The proxy then re-obfuscates the packet using standard obfuscated2 before sending it to Telegram.
This means that no third party can de-obfuscate or classify traffic between the client and the MTProto proxy.
- Pros: Traffic between the client and proxy looks like random data and cannot be de-obfuscated by ISPs, even with significant computing power. As a reverse proxy, clients don’t need to implement new protocols — just obfuscated2 and a field for the secret. The client connects to the MTProto proxy as if it’s a regular Telegram server.
- Cons: Each packet must be decrypted and re-encrypted on the proxy server. This is resource-intensive, so don’t expect as many stable public proxies as with SOCKS5. There’s still no official documentation or implementation examples from Telegram. Also, MTProto proxies cannot proxy voice call traffic, as voice data uses relay servers and a different protocol.
MTProto proxies can also force users to see a “sponsor channel,” allowing proxy owners to monetize their servers. You can only hide this channel by disconnecting from the proxy.
Conclusion
Thanks for reading! I hope this was interesting and clear. If you still have questions, try to find me and I’ll update the article. No contact info here — you’ll have to look for it 🙂
Subscribe to my channel! Please share this post to help end debates about how these methods work in technical communities.
Meow, yours truly, Anya ❤️