Russia Overtakes the US in Phishing Site Hosting
According to analysts at Group-IB, in 2019 the company blocked over 14,000 phishing resources—three times more than the previous year. Among the key trends of last year, CERT-GIB experts noted a shift in attack focus toward users of cloud storage services in both B2C and B2B segments. Additionally, phishers moved from creating single fraudulent pages to building entire networks of sites targeting specific brands, ensuring continuous operation and greater resistance to takedowns.
In the second half of 2019, CERT-GIB blocked 8,506 phishing resources, compared to 2,567 the year before. Overall, 14,093 phishing pages were blocked in 2019, up from 4,494 in 2018. This sharp increase is attributed not only to improved detection and identification of criminal schemes but also to changes in phishers’ tactics. Attackers now prolong their phishing campaigns, creating new pages to replace those that are blocked, rather than switching brands after takedowns. As a result, another trend was the growing complexity and expansion of phishing attack infrastructure.
Phishing Targets and Shifting Victim Pools
Group-IB data shows that in 2019, the largest share of phishing pages targeted online services (29.3%), cloud storage (25.4%), and financial organizations (17.6%). Researchers also noted that attackers revised their “victim pool.” The number of phishing attacks disguised as cloud storage services nearly doubled, and fraudulent pages targeting internet service provider users tripled.
The value of accessing a user’s cloud storage or personal account with a provider is clear: attackers are after personal or payment data stored there. The increased interest in cloud storage and ISP attacks was accompanied by a decline in phishing targeting email services—their share dropped from 19.9% to 5.9%—as well as cryptocurrency projects.
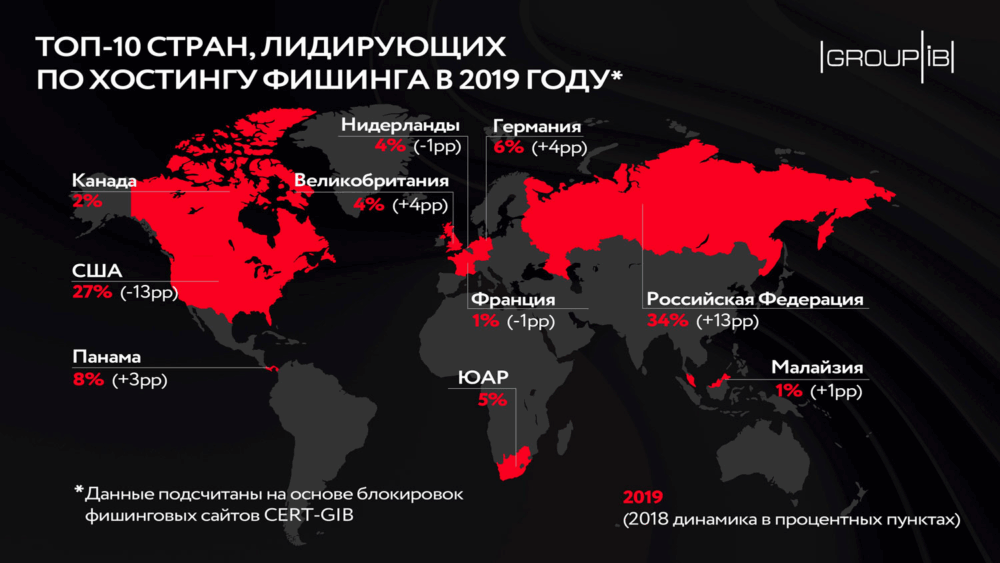
Russia Becomes the Top Host for Phishing Sites
Interestingly, 2019 marked a change in the leading country hosting phishing resources. The US, which held the top spot for several years (27%), was overtaken by Russia (34%). Panama remained in third place, accounting for 8% of blocked sites. Other countries in the top rankings included Germany, South Africa, the UK, the Netherlands, Canada, Malaysia, and France.
Email Remains the Main Malware Delivery Channel
The second half of 2019 saw no change in a long-standing trend: email remained the primary channel for delivering malware (ransomware, banking trojans, backdoors), used in 94% of analyzed cases. In most cases (98%), malware was hidden in attachments, while only 2% of phishing emails contained links to download malicious files. For comparison, in the first half of 2019, 23% of phishing emails contained such links, suggesting that attachments are more effective for attackers.
To bypass corporate security, attackers continued to archive malicious attachments. In the second half of 2019, about 70% of all malicious objects were delivered in archives, mainly using .rar (29%) and .zip (16%) formats. The password to decrypt the archive was provided in the email, subject line, archive name, or in further correspondence with the victim.
Most Common Malware in Phishing Emails
Ransomware remained the most common payload in phishing emails in the second half of 2019, making up 47% of all malicious attachments. Banking trojans continued to lose popularity, found in only 9% of malicious campaigns, giving way to spyware and backdoors (35%). This shift may be due to the growing functionality of backdoors, which can also be used to steal financial information.
The top 10 tools used by attackers in CERT-GIB-documented attacks in the second half of 2019 included:
- Troldesh ransomware (55%)
- Pony backdoor (11%)
- Formbook (5%)
- Nanocore (4%)
- Netwire (1%)
- RTM banker (6%)
- Emotet (5%)
- AgentTesla spyware (3%)
- Hawkeye (2%)
- Azorult (1%)
AgentTesla, Netwire, and Azorult were new threats observed during this period.
Expert Commentary
“In the second half of 2019, we observed an increase in the duration of phishing attacks—attackers changed their approach by expanding their resource base. Cloud storage and online services will remain the main targets for phishing operators due to the large amount of personal information stored there. Such targets allow attackers to first extract sensitive data and then blackmail victims for ransom,” summarized Yaroslav Kargalev, Deputy Head of CERT Group-IB.