PowerGhost: A New Fileless Miner with DDoS Capabilities
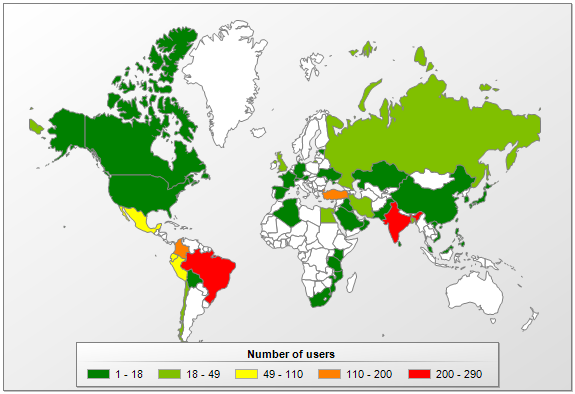
Researchers at Kaspersky Lab have discovered a new cryptominer called PowerGhost, which has been spreading across corporate networks worldwide, infecting both workstations and servers. Countries most affected by its attacks include Brazil, Colombia, India, and Turkey. In Russia, dozens of users have also been targeted.
PowerGhost is a fileless malware, meaning it resides in the device’s memory and does not require executable files to run, making it much harder to detect. Infection occurs through exploits or remote administration tools. The main part of the cryptominer is then loaded and executed without being saved to the hard drive.
Immediately after infection, cybercriminals can enable PowerGhost to automatically update itself, spread across the network, and begin cryptomining. In one version of PowerGhost, a tool for conducting DDoS attacks was also discovered. It is likely that the attackers planned to earn additional income from their mining botnet by offering DDoS-for-hire services.
Notably, incidents involving this new malware confirm recent predictions by Kaspersky Lab experts: developers of malicious cryptominers are indeed shifting to targeted attacks to increase their financial gains.
How PowerGhost Works
PowerGhost is an obfuscated PowerShell script containing the main code and additional modules, including:
- The miner itself
- Mimikatz (a tool for extracting credentials)
- The libraries msvcp120.dll and msvcr120.dll, required for the miner’s operation
- A module for reflective PE injection
- Shellcode for the EternalBlue exploit
The malware uses multiple fileless techniques to remain undetected by users and evade antivirus technologies. Infection occurs remotely using exploits or remote administration tools such as Windows Management Instrumentation (WMI). Upon infection, a one-line PowerShell script is executed, which downloads the main body of the malware and runs it immediately, without writing anything to the hard drive.