96% of Organizations Are Not Protected from Local Network Breaches
Positive Technologies experts have analyzed the security status of Russian companies. During penetration tests conducted in 2021-2022, it was found that 96% of organizations were not protected from breaches into their local networks: in every case, full control over the infrastructure was achieved. On average, it took five days and four hours to gain access to a company’s internal network.
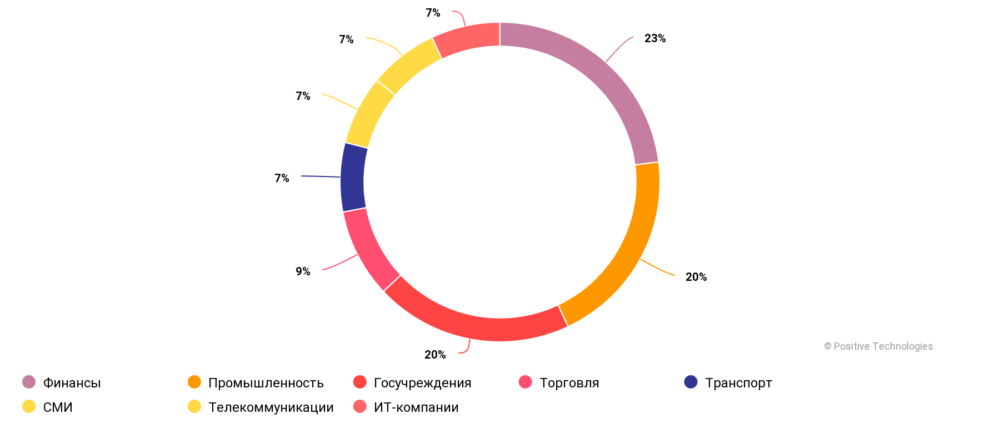
Distribution of Tested Organizations by Industry
The company’s report states that the level of protection against both external and internal threats in the analyzed companies was generally low. Numerous confirmed attack vectors targeting access to critical resources were discovered, and potential attackers did not need high-level skills to exploit these vulnerabilities.
Here are some key figures and findings from the experts’ report:
- In 96% of organizations, an attacker could breach the network perimeter and access the internal network.
- In 57% of companies, there was a penetration vector consisting of no more than two steps, with the average being four steps.
- The fastest attack was completed by penetration testers in just one hour.
- On average, it could take an attacker five days and four hours to breach a company’s internal network.
The main entry points into organizations’ networks were vulnerabilities and misconfigurations in web applications. Worse yet, such vectors were found in every company without exception.
Successful Attacks During External Penetration Tests
Among all penetration vectors involving web application vulnerabilities, 14% included the exploitation of zero-day vulnerabilities. A total of five such vulnerabilities were identified during external penetration tests.
Most often, critical vulnerabilities were related to weak password policies and lack of software updates. In half of the companies studied, critical vulnerabilities were found in web application code.
External penetration tests revealed that potential attackers could gain unauthorized access to confidential information in 9 out of 10 companies. For example, this could include trade secrets.
During internal penetration tests, it was proven possible to gain full control over domain resources in 100% of organizations, and access to confidential information was possible in 68% of companies. Examples of confidential information included customer personal data and company databases.
Security Levels of Tested Organizations
In 47% of the companies studied, specific penetration test objectives were set, and in 27% of those, verification of unacceptable events was conducted. Most often, the list of unacceptable events included theft of critical information, access to top management accounts, theft of funds, and disruption of key business processes.
“Among all the unacceptable events identified by organizations, 89% were proven to be possible,” commented Positive Technologies analyst Yana Yurakova. “On average, it would take attackers 10 days to carry out an unacceptable event. In some cases, this did not even require obtaining maximum privileges in the domain. Most of the unacceptable events that were proven possible are associated with potential reputational damage (61% of events), regulatory sanctions (57%), and financial losses (39%).”