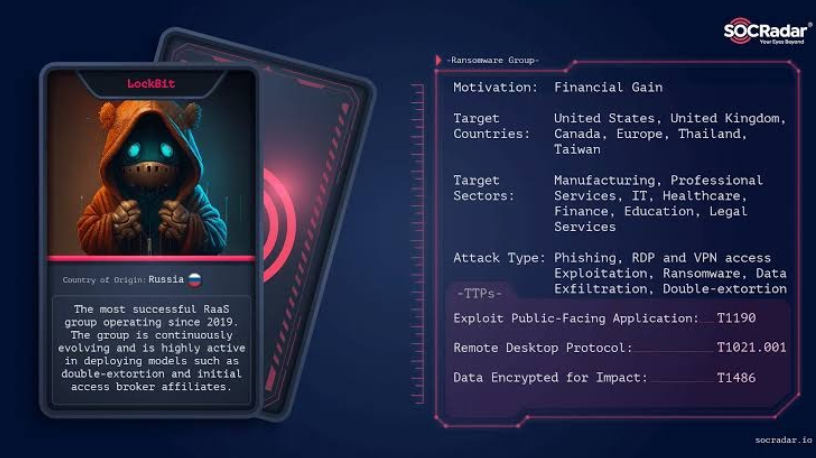
Police Arrest LockBit Members and Release Decryption Tool
Law enforcement agencies have shared new details about Operation Cronos, during which the infrastructure of the LockBit ransomware group was compromised. Authorities report the arrest of two LockBit members in Poland and Ukraine, as well as the seizure of over 200 cryptocurrency wallets. Additionally, a free decryption tool has been released to help victims recover files encrypted during LockBit attacks.
Operation Cronos
Operation Cronos was first reported earlier this week. As a result, many LockBit websites used for data leaks and negotiations with victims were taken offline and are now under the control of law enforcement. Authorities initially withheld details about the operation but are now gradually releasing more information, promising further updates in the future.
The international operation to disrupt LockBit was led by the UK’s National Crime Agency (NCA), with law enforcement from 11 countries coordinated by Europol and Eurojust. The investigation began in April 2022 at the request of French authorities.
According to Europol, “As a result of the months-long operation, the main LockBit platform and other critical infrastructure supporting this criminal organization were compromised. During the operation, 34 servers were seized in the Netherlands, Germany, Finland, France, Switzerland, Australia, the USA, and the UK.”
Europol representatives state that LockBit’s infrastructure is now under government control. During the operation, more than 14,000 accounts linked to data theft or the group’s infrastructure were identified. These accounts were used by LockBit to host attack tools and software, as well as to store files stolen from companies. Information about these accounts has now been handed over to law enforcement.
The NCA notes, “Some data in LockBit’s systems belonged to victims who paid ransoms. This shows that even if a ransom is paid, there is no guarantee the data will actually be deleted, despite the criminals’ promises.”
Authorities also extracted over 1,000 decryption keys from the seized LockBit servers. Using these keys, the Japanese police, NCA, and FBI, with support from Europol, created a free decryption tool for victims of LockBit 3.0 Black Ransomware attacks. This tool is now available on the No More Ransom portal.
Europol also claims to have collected “a huge amount of data” on LockBit’s operations, which will now be used in investigations targeting the group’s leaders, malware developers, and operators.
Arrests and Cryptocurrency Seizures
So far, only two arrests have been reported: in Poland and Ukraine, where two LockBit members were detained at the request of French authorities. Their identities have not been disclosed. Additionally, French and US authorities have issued three more international arrest warrants and published five indictments related to other group members.
“We have not arrested everyone connected to LockBit (the core group or its affiliates). This is a long-term process. We have now gathered a huge amount of information and will be closing in on these individuals, especially if they are in jurisdictions accessible to us. But now they all know we are watching them, searching for them, and they will always be looking over their shoulders,” said Jean-Philippe Lecouffe, Europol’s Deputy Executive Director of Operations, at a press conference.
The US Department of Justice has also filed charges in absentia against two Russian nationals, Artur Sungatov and Ivan Gennadievich Kondratyev (also known as Bassterlord), for their involvement in LockBit attacks.
It is alleged that since January 2021, Sungatov used LockBit ransomware to attack “manufacturing, logistics, insurance, and other companies located in Minnesota, Indiana, Puerto Rico, Wisconsin, Florida, and New Mexico.”
According to the Department of Justice, Kondratyev used LockBit since August 2021, targeting “municipal and private entities in Oregon, Puerto Rico, and New York, as well as other targets in Singapore, Taiwan, and Lebanon.” In a separate indictment, Kondratyev is also linked to the use of REvil malware in 2020 to extort money from an unnamed company in Alameda County.
The US Treasury Department has announced sanctions against both Sungatov and Kondratyev.
Notably, the data leak site previously used by hackers to publish stolen information and blackmail companies is now being used to leak information about LockBit itself.
Based on countdown timers, authorities may reveal the identity of the group’s administrator, known as Lockbitsupp, by the end of the week (or offer a large reward for information about them), and will also disclose information about the hackers’ cryptocurrency assets. Reports from SecureWorks and TrendMicro on LockBit and its malware are also expected to be published.
Among the data already released by law enforcement are screenshots of LockBit’s backend systems.
As for the seized cryptocurrency wallets, it is not yet known how much money they contained. However, it is possible that some companies affected by LockBit attacks may be able to recover ransom payments, similar to what happened with Colonial Pipeline in 2021.