New macOS Backdoor Discovered in Pirated Software
Experts at Kaspersky Lab have discovered a previously unknown malware family targeting macOS, which spreads through pirated software. The payload is a backdoor capable of executing any scripts with administrator privileges and replacing installed cryptocurrency wallet apps, such as Exodus and Bitcoin, with infected versions.
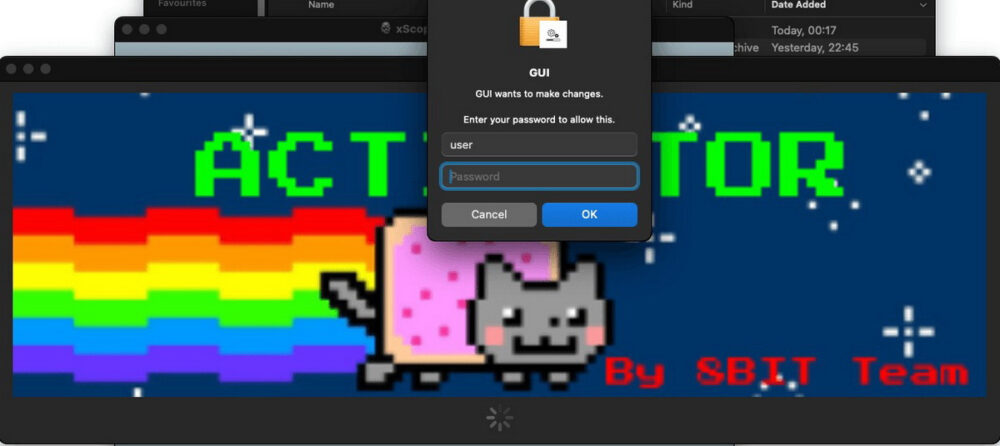
The malicious campaign targets macOS 13.6 and above, affecting both Intel-based and Apple Silicon devices. The compromised disk images contain not only the pirated software but also an activator, which the user is prompted to run to “patch” the application.
The activator appears simple, featuring only a “PATCH” button. When clicked, the system requests the user’s password.
How the Malware Works
Researchers quickly discovered that the activator is more complex than it seems. It stores a Python 3.9.6 installer package and an additional Mach-O file named tool in the Resources folder. The main file, a Fat Mach-O named GUI, implements the “PATCH” button. When pressed, two actions occur:
- The Python installer is copied to the
/tmp/directory for temporary files. - The
toolexecutable from the resources folder is launched with administrator privileges, using the outdatedAuthorizationExecuteWithPrivilegesfunction, which prompts for the admin password.
The “patching” of the pirated application genuinely takes place: tool compares the first 16 bytes of the executable with a sequence embedded in the activator’s code and removes them if they match.
Interestingly, after this process, the application becomes functional and is indeed “cracked.” Attackers use already cracked versions of apps but add a few bytes to the beginning of the executable to break it, forcing users to run the activator.
Malicious Payload and Communication
After patching, the main malicious payload is executed. The malware connects to a command-and-control (C2) server and downloads an encrypted script. It uses an unusual method to communicate with the C2 and hide its activity in network traffic, almost guaranteeing the payload will be delivered.
To obtain the server address, the program assembles a URL from two lists of words embedded in its code, adding a random five-letter sequence as a third-level domain. It then queries a DNS server for the TXT record of this domain. Since TXT records can contain various domain information, such a request appears normal.
After testing possible word combinations, researchers found that only one second-level domain was active: imohub[.]net. The third-level domain can be any value, as long as it is present in the request.
The DNS server’s response contains three TXT records, which the program processes and combines into a complete message. Each record is a Base64-encoded part of the ciphertext, with the first byte indicating its order (removed during assembly). The ciphertext is encrypted with AES in CBC mode. The decrypted message is a Python script.
This script contacts apple-health[.]org every 30 seconds to download and execute the next script, which runs for 14,400 seconds (4 hours) before being replaced by a new version.
Backdoor Capabilities and Data Theft
The Python script reveals the attackers’ goals: executing arbitrary commands received from the server. These commands are also Python scripts, encoded in Base64. In addition to executing commands, the script collects and sends the following information to the server:
- Operating system version
- List of directories in
/Users/ - An empty
avfield, likely for antivirus information in future versions - List of installed applications
- Processor type
- Device’s external IP address
- An empty
verfield, possibly for the malware version
At the time of research, the server was not returning any commands and eventually stopped responding. However, when researchers downloaded the third-stage Python script again, they found changes in the metadata (such as the C2 server’s IP address, domain, GUID, and program version), which seem to update automatically as the server’s IP changes every 10–20 minutes. There were also functional code changes, indicating the campaign is still under development.
Targeting Cryptocurrency Wallets
The script contains two notable functions: check_exodus_and_hash() and check_btccore_and_hash(). Both reference the domain apple-analyser[.]com, used to host additional downloads.
These functions check if the corresponding cryptocurrency wallet app is present on the device. If found, they replace it with a version downloaded from apple-analyser[.]com. The malicious app then steals the password used to unlock the wallet, as well as the wallet itself, its name, and balance.