Hacker Error Makes Stolen Data Accessible Through Google
Hackers who targeted thousands of organizations worldwide in a large-scale phishing campaign accidentally left their stolen data unprotected, making it accessible through Google search. The phishing campaign, which lasted for over six months, used dozens of domains with fake Microsoft Office 365 login pages. Despite relying on very simple techniques, the attackers managed to bypass email security filters and collected at least 1,000 login credentials for corporate Microsoft Office 365 accounts.
According to researchers from Check Point and Otorio who investigated the campaign, the hackers mistakenly made the stolen data available on the open internet. Experts explained that the attackers stored the stolen information on specially registered domains, but placed the data in a publicly accessible file, which was then indexed by Google’s search engine.
The researchers also found that the hackers compromised legitimate WordPress servers to host phishing PHP pages. Cybercriminals prefer using hacked servers over their own infrastructure because compromised sites have a good reputation, making their phishing attempts less suspicious.
After analyzing information from about 500 records, the researchers determined that the most frequent victims of the phishing campaign were companies in the construction sector (16.7%), energy sector (10.7%), and information technology sector (6.0%).
Phishing Tactics Used
To lure victims to fraudulent pages, the attackers used several tactics in their phishing emails. The “Subject” field often included the victim’s name or company name, and the attachment contained a scanned notification in HTML format.
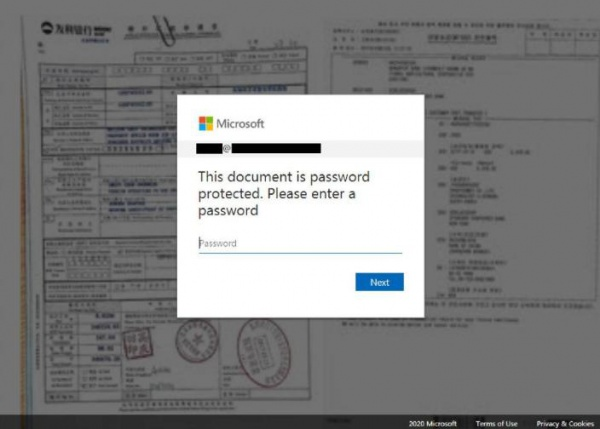
When the attachment was opened in a web browser, a blurred image appeared with a fake Microsoft Office 365 login form overlaid. The form stated, “This document is password protected. Please enter the password.” The username field was already filled in with the victim’s email address, which helped avoid suspicion.
In the background, JavaScript code checked the credentials entered by the victim, sent them to a server controlled by the attackers, and then redirected the victim to the real Microsoft Office 365 login page to distract them from the phishing attempt.
Bypassing Detection
To avoid detection, the hackers sent phishing emails from compromised mailboxes. For example, in one attack, the criminals posed as the German hosting provider IONOS by 1&1. Although the phishing campaign began in August 2020, researchers also found phishing emails dated as early as May 2020.