Fake VPN Chrome Extensions Force-Installed 1.5 Million Times
Researchers at ReasonLabs have discovered three malicious Chrome browser extensions disguised as VPNs. These extensions were downloaded 1.5 million times and actually functioned as infostealers and cashback theft tools.
The dangerous extensions were force-installed on victims’ browsers and spread through installers hidden in pirated copies of popular games such as Grand Theft Auto, Assassin’s Creed, and The Sims 4, which were downloaded from torrent trackers.
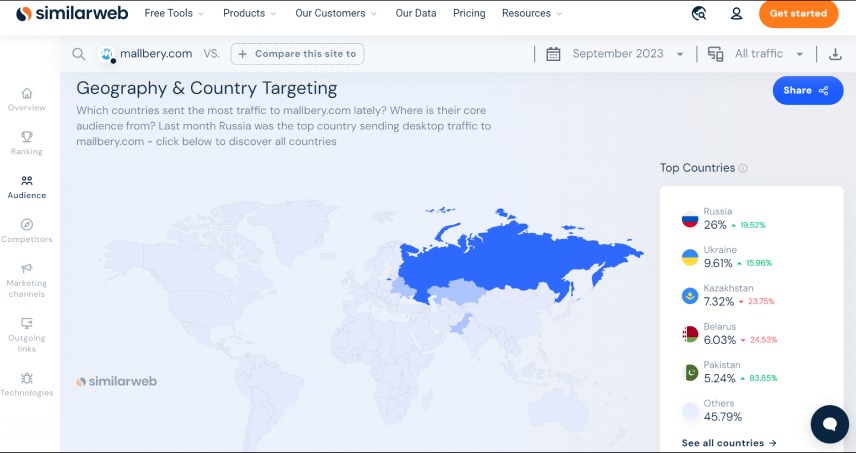
According to experts, most infections occurred in Russia, Ukraine, Kazakhstan, and Belarus, as the campaign appeared to specifically target Russian-speaking users.
Details of the Malicious Extensions
- netPlus – 1 million installations
- netSave – 500,000 installations
- netWin – 500,000 installations
ReasonLabs has already notified Google about the issue, and the company has removed the malicious extensions from the Chrome Web Store. However, by that time, the total number of installations had already surpassed 1.5 million.
How the Extensions Were Installed
Researchers found over a thousand different torrent files containing a malicious installer, which was an Electron application ranging from 60 to 100 MB in size. The installer checked for antivirus products on the infected machine, then installed netSave in Google Chrome and netPlus in Microsoft Edge.
The report highlights that the fake VPN extensions were installed automatically at the registry level, requiring no user interaction or action. To create a sense of legitimacy, the fake extensions even featured realistic user interfaces and appeared to offer paid subscriptions.
Capabilities and Risks
Code analysis showed that the extensions had access to permissions such as tabs, storage, proxy, webRequest, webRequestBlocking, declarativeNetRequest, scripting, alarms, cookies, activeTab, management, and offscreen. Abuse of the offscreen permission allowed the malware to run scripts via the Offscreen API and secretly interact with the web page’s DOM (Document Object Model). This access enabled the theft of confidential user data, manipulation of web requests, and even disabling of other installed extensions.
Another notable feature of the malware was its ability to disable other extensions related to cashback and coupons, eliminating competitors on the infected device and redirecting all profits to the attackers. According to ReasonLabs, the malware targeted over 100 such extensions, including Avast SafePrice, AVG SafePrice, Honey: Automatic Coupons & Rewards, LetyShops, Megabonus, AliRadar Shopping Assistant, Yandex.Market Adviser, ChinaHelper, and Backlit.
Recommendations for Users
Researchers recommend that users regularly check which extensions are installed in their browsers and review new feedback in the Chrome Web Store to ensure that others are not reporting malicious behavior.