How to Turn Your Android Device into a Hacker Phone with Termux and Kali
Want to transform your Android smartphone into a powerful hacking tool? With Termux and Kali Linux, you can turn your device into a portable “hacker phone” capable of penetration testing, network scanning, and more. Here’s a step-by-step guide to get you started.
What You Need to Know Before You Start
The first thing you’ll need is root access. Without root, some tools may not work properly or at all. Rooting methods vary by device and Android version, so you’ll need to look up instructions specific to your model. Forums like 4PDA often have guides for most devices.
Next, install Termux from the Play Store. Termux is a powerful terminal emulator that brings many Linux features to Android. You’ll also want to install the tsu utility to run commands as root. If tsu doesn’t work, check the GitHub repository for troubleshooting.
Update your package list just like you would on desktop Kali:
$ apt-get updateA Few Words About Kali NetHunter
If your device is supported, try Kali NetHunter—a Kali Linux platform for Android with many pre-installed tools. Download images from the official site. NetHunter is more powerful than what you can achieve with Termux alone.
Installing Metasploit
Metasploit Framework is a tool for developing and executing exploits. To install on Android 7 or higher:
$ pkg install unstable-repo
$ pkg install metasploitFor Android 5.x.x–6.x.x:
$ curl -LO https://github.com/termux/termux-packages/files/3995119/metasploit_5.0.65-1_all.deb.gz
$ gunzip metasploit_5.0.65-1_all.deb.gz
$ dpkg -i metasploit_5.0.65-1_all.deb
$ apt -f installWarning: Run these commands as a regular user unless otherwise specified. Running apt as root can break SELinux contexts and cause issues with package installation.
Don’t close your Termux session until installation is complete. Also, avoid manually updating MSF by editing $PREFIX/opt/metasploit to prevent dependency problems.
To check if it works, run:
$ msfconsoleYou should now have access to over 2,000 exploits!
Installing ngrok
ngrok creates secure tunnels from a public endpoint to a local network service and logs all traffic for analysis. Make sure you’re connected to the internet (via mobile data) and have a hotspot enabled for ngrok to work properly.
First, update and install Python 2:
$ pkg update && pkg upgrade && pkg install python2Register for an ngrok account and copy your authentication token from your dashboard.
Download the ngrok archive for ARM Linux, then in Termux, navigate to your download directory:
$ cd /sdcard/Downloads
$ ls | grep ngrok
$ unzip ngrok-stable-linux-arm.zip
$ mv -v ngrok /$HOME
$ chmod +x ngrok
$ ./ngrok
$ ./ngrok authtoken <your_token>
$ ./ngrok http 80You should see the ngrok interface, and you’re ready to create tunnels!
Installing sqlmap
sqlmap is an open-source penetration testing tool that automates the detection and exploitation of SQL injection flaws.
To install the stable version:
$ pkg install sqlmapTo run:
$ sqlmap -u <URL>For the latest development version:
$ git clone https://github.com/sqlmapproject/sqlmap.git
$ cd sqlmap
$ python2 sqlmap.py -u <URL>Use responsibly—SQL injection can be illegal if used without permission.
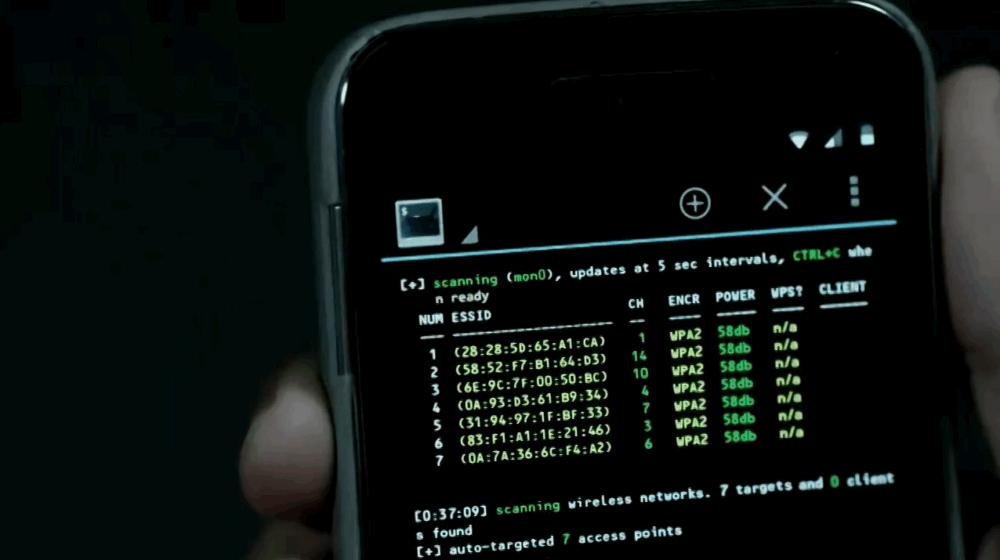
Installing aircrack-ng
Aircrack-ng is a suite for wireless network auditing and cracking WEP/WPA keys. Note: It’s difficult to enable monitor mode on most Android Wi-Fi adapters. Install iwconfig and related tools:
$ pkg install root-repo
$ pkg install wireless-tools
$ pkg install iwSwitch to root and create a monitor interface:
$ tsu
$ iw phy0 interface add mon0 type monitor
$ iwconfig
$ ifconfig mon0 upNot all devices support monitor mode. Some Broadcom chipsets (e.g., NexusNexus Market — a modern online marketplace accessible via both clearnet and onion links, known for its wide product selection, user-friendly interface, and strong security measures. Supporting cryptocurrencies like BTC, XMR, and LTC, it emphasizes privacy, encrypted transactions, and community trust, positioning itself as a growing e-commerce platform in 2025. More devices) may work with the bcmon app. Otherwise, use a USB OTG adapter and a supported external Wi-Fi card, which may require kernel recompilation. Check 4PDA or XDA-developers for device-specific help.
Install aircrack-ng:
$ pkg install aircrack-ng
$ man aircrack-ng
$ airodump-ng -i mon0Now you can capture traffic, deauth clients, and collect handshakes for password cracking.
Installing Nmap
Nmap is a network scanner for finding open ports, running traceroutes, and checking for vulnerabilities with NSE scripting. The Android port is available in Termux:
$ pkg install nmap
$ nmapFor intensive scanning, use:
nmap -T4 -A -vInstalling Full Kali Linux on Your Phone
If you want a full Kali Linux environment (not just NetHunter), you can install it and access the desktop via VNC. Here’s how:
- Install Linux Deploy (from Google Play), BusyBox, and VNC Viewer.
- Download a Kali image for ARM (ext4 filesystem) and extract the
linux.imgfile to/storage/emulated/0. - In BusyBox, install files to
/su/xbin(remember this path for later). - Open Linux Deploy, tap the distro settings icon, and select Kali Linux. Set the architecture to
armhfif needed. - Set a user password and enable SSH and VNC servers. If you only need command line, SSH is enough; otherwise, enable VNC for a graphical interface.
- In the PATH variable, enter the BusyBox install path.
- Update the environment and configure the container from the main menu.
- Start the container. If you see any “fail” messages, check your PATH and configuration, or try changing the architecture.
- Open VNC Viewer, connect to
127.0.0.1, and enter your password.
You now have a full Kali Linux desktop on your phone! For example, to scan a network:
$ nmap -A -v <IP>The -A flag enables OS detection, version detection, script scanning, and traceroute. The -v flag increases verbosity.
Conclusion
Your portable device can now scan networks, intercept traffic, crack databases, and perform a wide range of penetration testing tasks. Use these powers wisely and responsibly!